Dynamic Reviewer is made over 3 solutions: HAST (IAST+RASP/wiki/spaces/KC/pages/1645674518), DAST and APM.
| Table of Contents |
|---|
DAST-Penetration Testing made easy
With Dynamic Reviewer Light-PenTest module, Security Reviewer becomes an hybrid solution. You can inspect your web application during running, directly from Security Reviewer, from Eclipse or other IDE plugins like Visual Studioyour Desktop, or using a Browser.
The following installation options are available:
Desktop for Windows, Linux or Mac. It is based on a re-engineered version of IronWasp, but using our own Core Engine, and offers additional professional features for Pen Testers, like deep discovery, plugin development console and HTTP Requests manipulation.
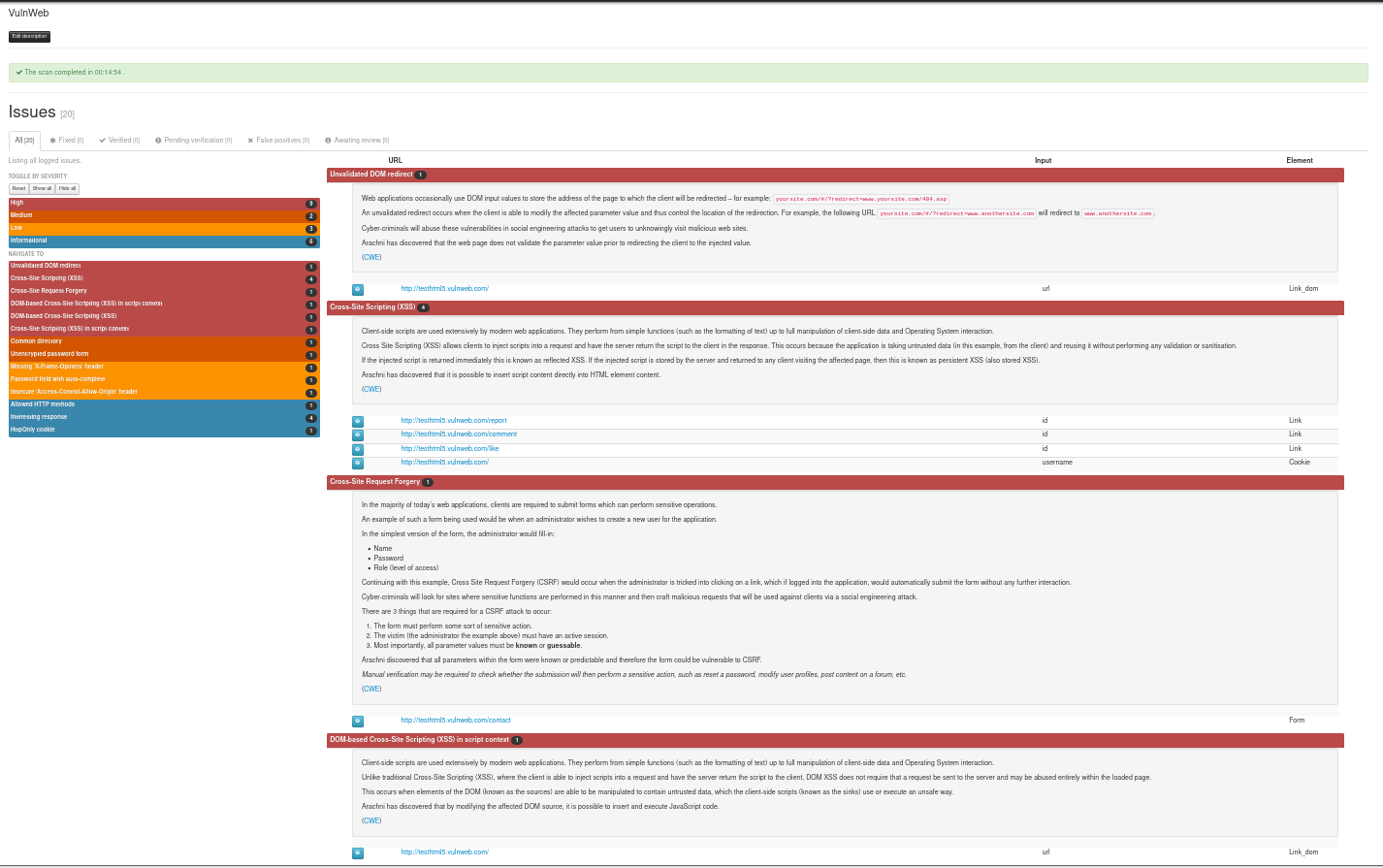
Web App on premise. It is based on Arachni Web UI, but using our own Core Engine. With Arachni we share also the Dispatcher Infrastructure via Arachni-rpc protocol, and the results in AFR format.
Command Line Interface. It is our own multi-platform Core Engine, 100% written by us using Python and C++ and started by scratch in 2015, covering 200% more Security Checks than the market leaders
Cloud. Our Web App offered in an high-performance European or American Secured Cloud Infrastructure
Its special lightweight PenTest features, allowing to explore vulnerabilities in your Web Applications at the same time to keeping the software securely in your own hands, at your premises. No need of Backups before PenTest, we guarantee our tool will keep your system and database integrity.
Dynamic Reviewer DAST plugins based architecture provides an VB.NET, Python and Ruby Scripting Environment with API (Desktop version), with full access to all functionality of the tool, for creating precise Crawlers and Scanners, used by the Pen Testers to write their own fuzzers, create custom crafted request, analysis of logs, etc.
Dynamic Reviewer DAST provides a robust and stable framework for Web Application Security Testing, suitable for all Security Analysts, QA and Developers with False Positives and False Negatives support. It is designed for optimum mix of Manual and Automated Testing and allows designing customised penetration tests, offering an easy-to-use GUI and advanced scripting capabilities.
Best Performances
Scan-times using traditional tools can range between a few hours to a couple of weeks – maybe even more. This means that wasted time can easily pile up, even when we’re talking about mere milliseconds per request/response.
Dynamic Reviewer benefits from great network performance due to its asynchronous HTTP request/response model. In this case – and from a high-level perspective –, asynchronous I/O means that you can schedule operations in such a way that they appear like they’re happening at the same time, which in turn means higher efficiency and better bandwidth utilization.
It provides a high-performance environment for the tests that need to be executed while making adding new tests very easy. Thus, you can rest assured that the scan will be as fast as possible and performance will only be limited by your or the audited server’s physical resources.
Avoiding useless technical details, the gist is the following:
...
Talk is cheap though, so let’s look as some numbers:
Duration | RAM | HTTP requests | HTTP requests/second | Browser jobs | Seconds per browser job | |
|---|---|---|---|---|---|---|
New engine | 00:02:14 | 150MB | 14,504 | 113.756 | 211 | 1.784 |
Old | 00:06:33 | 210MB | 34,109 | 101.851 | 524 | 3.88 |
Larger real production site (cannot disclose) | ||||||
|---|---|---|---|---|---|---|
Duration | RAM | HTTP requests | HTTP requests/second | Browser jobs | Seconds per browser job | |
New engine | 00:45:31 | 617MB | 60,024 | 47.415 | 9404 | 2.354 |
Old | 12:27:12 | 1,621MB | 123,399 | 59.516 | 9180 | 48.337 |
As you can see, the impact of the improvements becomes more substantial as the target’s complexity and size increases, especially when it comes to scan duration and RAM usage — and for the production site the new engine consistently yielded better coverage, which is why it performed more browser jobs.
...
The list of DOM Security Issues found by Dynamic Reviewer are:
# | Issue | Type | Category |
1 | Code Injection - Client Side | Error | Code Execution |
2 | Code Injection - PHP input wrapper | Error | Code Execution |
3 | Code injection - Timing | Error | Code Execution |
4 | File Inclusion - Client Side | Error | Code Execution |
5 | OS Command Injection - Client Side | Error | Code Execution |
6 | OS Command Injection - Timing | Error | Code Execution |
7 | Remote File Inclusion Client Side | Error | Code Execution |
8 | Session Fixation | Error | Code Execution |
9 | XSS - DOM | Error | Code Execution |
10 | XSS - DOM - Script Context | Error | Code Execution |
11 | XSS - Event | Error | Code Execution |
12 | Data from attacker controllable navigation based DOM properties is executed as HTML | Error | Code Execution |
13 | Data from attacker controllable navigation based DOM properties is executed as JavaScript | Error | Code Execution |
14 | Data from attacker controllable URL based DOM properties is executed as HTML | Error | Code Execution |
15 | Data from attacker controllable URL based DOM properties is executed as JavaScript | Error | Code Execution |
16 | Non-HTML format Data from DOM storage is executed as HTML | Warning | Code Execution |
17 | Non-JavaScript format Data from DOM storage is executed as JavaScript | Warning | Code Execution |
18 | HTML format Data from DOM storage is executed as HTML | Info | Code Execution |
19 | JavaScript format Data from DOM storage is executed as JavaScript | Info | Code Execution |
20 | Data from user input is executed as HTML | Warning | Code Execution |
21 | Data from user input is executed as JavaScript | Warning | Code Execution |
22 | Non-HTML format Data taken from external site(s) (via Ajax, WebSocket or Cross-Window Messages) is executed as HTML | Error | Code Execution |
23 | Non-JavaScript format Data taken from external site(s) (via Ajax, WebSocket or Cross-Window Messages) is executed as JavaScript | Error | Code Execution |
24 | HTML format Data taken from external site(s) (via Ajax, WebSocket or Cross-Window Messages) is executed as HTML | Warning | Code Execution |
25 | JavaScript format Data taken from external site(s) (via Ajax, WebSocket or Cross-Window Messages) is executed as JavaScript | Warning | Code Execution |
26 | Non-HTML format Data taken from across sub-domain (via Ajax, WebSocket or Cross-Window Messages) is executed as HTML | Warning | Code Execution |
27 | Non-JavaScript format Data taken from across sub-domain (via Ajax, WebSocket or Cross-Window Messages) is executed as JavaScript | Warning | Code Execution |
28 | HTML format Data taken from across sub-domain (via Ajax, WebSocket or Cross-Window Messages) is executed as HTML | Info | Code Execution |
29 | JavaScript format Data taken from across sub-domain (via Ajax, WebSocket or Cross-Window Messages) is executed as JavaScript | Info | Code Execution |
30 | Non-HTML format Data taken from same domain (via Ajax, WebSocket or Cross-Window Messages) is executed as HTML | Warning | Code Execution |
31 | Non-JavaScript format Data taken from same domain (via Ajax, WebSocket or Cross-Window Messages) is executed as JavaScript | Warning | Code Execution |
32 | HTML format Data taken from same domain (via Ajax, WebSocket or Cross-Window Messages) is executed as HTML | Info | Code Execution |
33 | JavaScript format Data taken from same domain (via Ajax, WebSocket or Cross-Window Messages) is executed as JavaScript | Info | Code Execution |
34 | Weak Hashing algorithms are used | Error | Cryptography |
35 | Weak Encryption algorithms are used | Error | Cryptography |
36 | Weak Decryption algorithms are used | Error | Cryptography |
37 | Cryptographic Hashing Operations were made | Info | Cryptography |
38 | Encryption operations were made | Info | Cryptography |
39 | Decryption operations were made | Info | Cryptography |
40 | Potentially Sensitive Data is leaked (via HTTP, Ajax, WebSocket or Cross-Window Messages) | Error | Data Leakage |
41 | Potentially Sensitive Data is leaked through Referrer Headers | Error | Data Leakage |
42 | Data is leaked through HTTP | Warning | Data Leakage |
43 | Data is leaked through WebSocket | Warning | Data Leakage |
44 | Data is leaked through Cross-Window Messages | Warning | Data Leakage |
45 | Data is leaked through Referrer Headers | Warning | Data Leakage |
46 | Potentially Sensitive Data is stored on Client-side Storage (in LocalStorage, SessionStorage, Cookies or IndexedDB) | Warning | Data Storage |
47 | Data is stored on Client-side Storage (in LocalStorage, SessionStorage, Cookies or IndexedDB) | Info | Data Storage |
48 | Cross-window Messages are sent insecurely | Error | Communication |
49 | Cross-site communications are made | Warning | Communication |
50 | Communications across sub-domains are made | Warning | Communication |
51 | Same Origin communications are made | Info | Communication |
52 | JavaScript code is loaded from Cross-site Sources | Warning | JS Code |
53 | JavaScript code is loaded from across sub-domains | Info | JS Code |
54 | JavaScript code is loaded from Same Origin | Info | JS Code |
Browser Cluster
The browser-cluster is what coordinates the browser analysis of resources (automated Web UI Clients) and allows the system to perform operations which would normally be quite time consuming in a high-performance fashion.
...
It provides the single point of contact that will contact its grid of Dispatch Servers (Dispatchers) with initial scan requests. The Dispatchers then spawn a new Instance on that Server. At this point, the Web UI Clients will be able to communicate directly with the spawned Instance to configure it for the appropriate scanning jobs. When an Instance is done with its task, The Web UI Clients pull the data and store it, while the Instance simply goes away, returning the resources it consumed to the operating system for future Instances or other software tasks altogether. As we move into production testing, we can scale the deployment to span additional resources on other servers in our grid, and this will not only allow us to run multiple scans, but accommodate teams of users while consolidating the data gathered in a central database on the Web UI Client.
...
Configuration options include:
...
Dynamic Reviewer DAST automatically Import Security Reviewer's Static Analysis the analyzed Web Application's directory and file lists, Attack Vectors and Exploits.
...
DISCLAIMER: Due we make use of opensource third-party components, we do not sell the product, but we offer a yearly subscription-based Commercial Support to selected Customers.
COPYRIGHT (C) 2014-2021 SECURITY REVIEWER SRL. ALL RIGHTS RESERVED.