With Dynamic Reviewer Light-PenTest module, Security Reviewer becomes an hybrid solution. You can inspect your web application during running, directly from your Desktop, or using a Browser.
...
The following installation options are available:
Desktop for Windows, Linux or Mac. It is based on a re-engineered version of IronWasp, but using our own Core Engine, and offers additional professional features for Pen Testers, like deep discovery, plugin development console and HTTP Requests manipulation.
Web App on premise. It is based on Arachni Web UI, but using our own Core Engine. With Arachni we share also the Agent Infrastructure via Arachni-rpc protocol, and the results in AFR format.
Command Line Interface. It is our own multi-platform Core Engine, 100% written by us using Python and C++ and started by scratch in 2015, covering 200% more Security Checks than the market leaders
Cloud. Our Web App offered in an high-performance European or Cloud. Our Web App offered in an high-performance European or American Secured Cloud Infrastructure
Its special lightweight PenTest features, allowing to explore vulnerabilities in your Web Applications at the same time to keeping the software securely in your own hands, at your premises. No need of Backups before PenTest, we guarantee our tool will keep your system and database integrity.
...
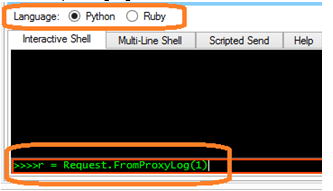
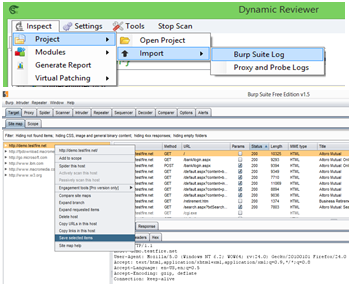
Dynamic Reviewer DAST plugins based architecture provides an VB.NET, a Python and Ruby Scripting Environment with API (Desktop version), with full access to all functionality of the tool, for creating precise Crawlers and Scanners, used by the Pen Testers to write their own fuzzers, create custom crafted request, analysis of logs, etc.
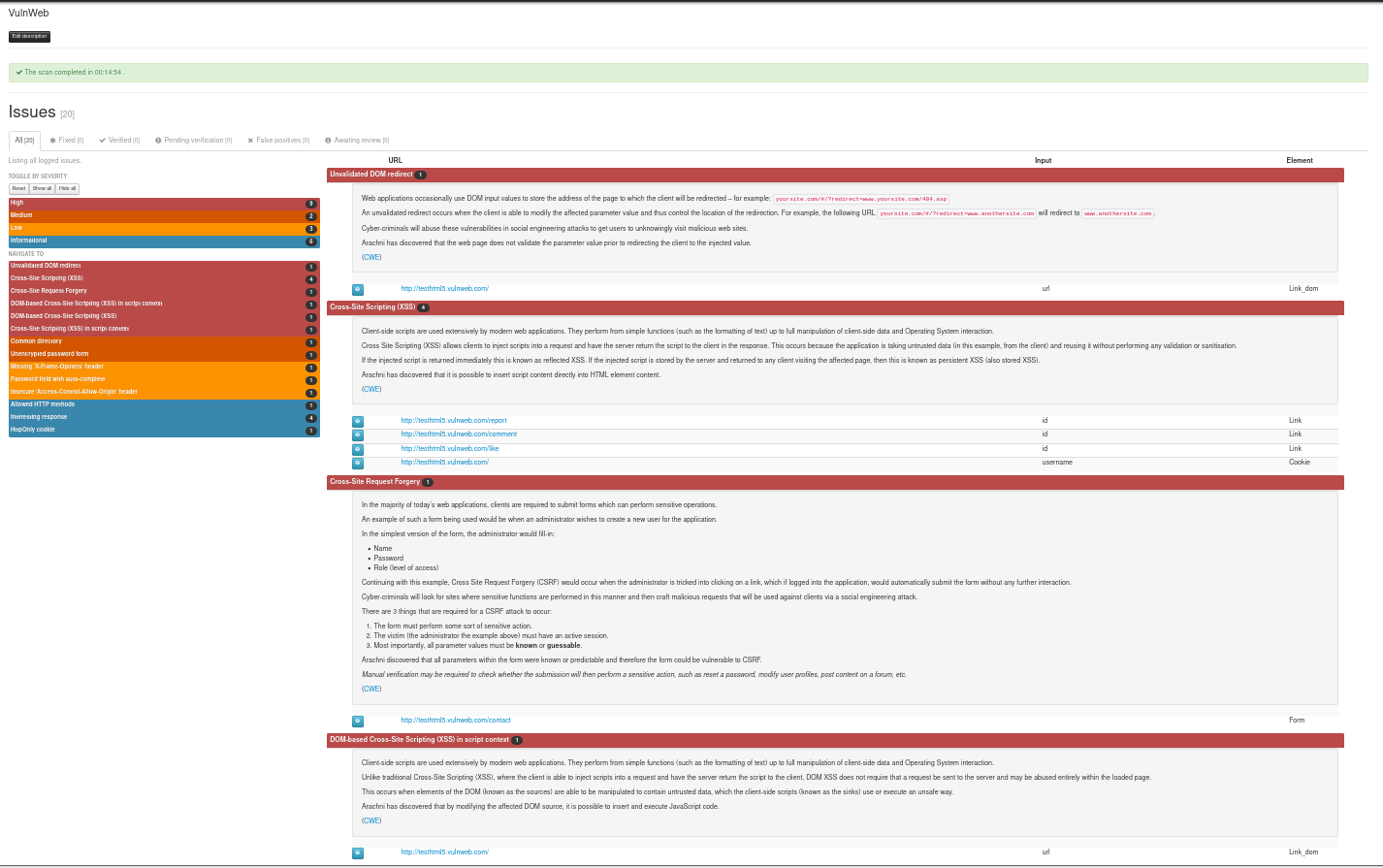
Dynamic Reviewer DAST provides a robust and stable framework for Web Application Security Testing, suitable for all Security Analysts, QA and Developers with False Positives and False Negatives support. It is designed for optimum mix of Manual and Automated Testing and allows designing customised penetration tests, offering an easy-to-use GUI and advanced scripting capabilities.
Best Performances
Scan-times using traditional tools can range between a few hours to a couple of weeks – maybe even more. This means that wasted time can easily pile up, even when we’re talking about mere milliseconds per request/response.
Dynamic Reviewer benefits from great network performance due to its asynchronous HTTP request/response model. In this case – and from a high-level perspective –, asynchronous I/O means that you can schedule operations in such a way that they appear like they’re happening at the same time, which in turn means higher efficiency and better bandwidth utilization.
It provides a high-performance environment for the tests that need to be executed while making adding new tests very easy. Thus, you can rest assured that the scan will be as fast as possible and performance will only be limited by your or the audited server’s physical resources.
Avoiding useless technical details, the gist is the following:
...
It provides the single point of contact that will contact its grid of Dispatch Servers (Agents) with initial scan requests. The Agents then spawn a new Instance on that Server. At this point, the Web UI Clients will be able to communicate directly with the spawned Instance to configure it for the appropriate scanning jobs. When an Instance is done with its task, The Web UI Clients pull the data and store it, while the Instance simply goes away, returning the resources it consumed to the operating system for future Instances or other software tasks altogether. As we move into production testing, we can scale the deployment to span additional resources on other servers in our grid, and this will not only allow us to run multiple scans, but accommodate teams of users while consolidating the data gathered in a central database on the Web UI Client.
...
Configuration options include:
...
Forms
Along with ones that require interaction via a real browser due to DOM events.
User-interface Forms
Input and button groups which don't belong to an HTML
<form>element but are instead associated via JS code.
User-interface Inputs
Orphan
<input>elements with associated DOM events.
Links
Along with ones that have client-side parameters in their fragment, i.e.:http://example.com/#/?param=val¶m2=val2
With support for rewrite rules.
Link Templates -- Allowing for extraction of arbitrary inputs from generic paths, based on user-supplied templates -- useful when rewrite rules are not available.
Along with ones that have client-side parameters in their URL fragments, i.e.:http://example.com/#/param/val/param2/val2
Cookies
Headers
Generic client-side elements which have associated DOM events.
AJAX-request parameters.
JSON request data.
XML request data.
...
Finally, Dynamic Reviewer will always apply on the side of caution and send all available payloads when it fails to identify specific platforms.
Unique Desktop Features
Our Desktop solution has the following features:
Built-in Crawler, Scan Manager and Proxy
...
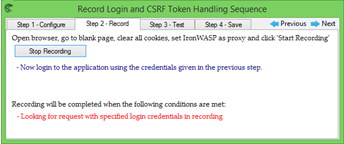
Login Sequence Recording
C#, VB.NET, Python and Ruby based Plugins, compatible with Burp Suite, Acunetix, TrustWare (formerly Cenzic) scripts and IronWASP API. Comes bundled with a growing number of Modules built by researchers in the security community
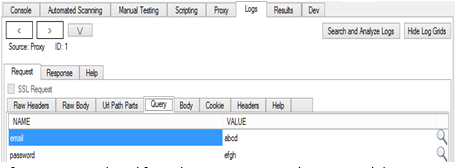
Burp suite Logs import. It can analyse the HTTP logs for Access Control and other checks
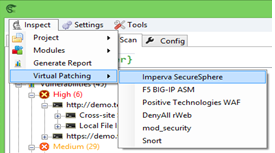
Virtual Patching to WAFs, like Imperva, F5, Positive Technologies, Snort, ModSecurity, DenyAll rWeb
Active plugins for Scanning, performing scans against the target to identify vulnerabilities, with fine-grained scanning support. Can be executed only when the user explicitly calls them. (e.g. Cross-Site Scripting, SQL Injection, Code Injection, Parameter Manipulation)
Passive plugins for Vulnerability detection, through analysis of all traffic going through the tool (e.g. passwords sent over clear-text and Insecure cookies)
Format plugins for defining data formats, to deal with various data formats in Request body, like JSON, XML, Java Serialized objects, AMF, WCF, GWT, Multi-part POST or custom data formats
Session plugins to customise the scans. Unique feature that can understand slight variations in Authentication, Session handling, CSRF protections and Log-flows/Multi-step forms
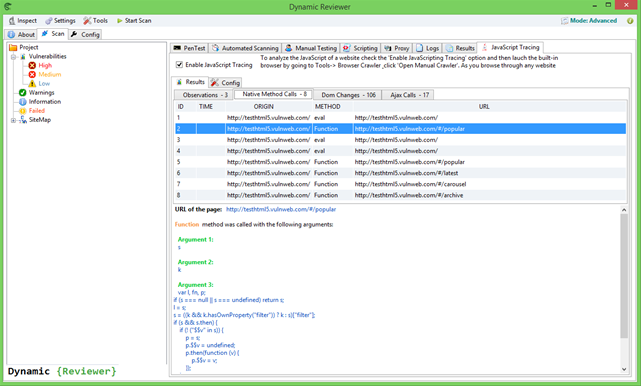
JavaScript Static Analysis Engine. It performs Taint Analysis for DOM-based XSS. Identifies Source and Sink objects and can trace them through the code
Exploits testing (integrated with Security Reviewer)
Dynamic Reviewer DAST automatically Import Security Reviewer's Static Analysis the analyzed Web Application's directory and file lists, Attack Vectors and Exploits.
HTML5 discovery. It performs JavaScript based port scans, stealth AppCache attacks and HTML5 botnets
Browser Phishing Framework. It perform multiple browser phishing attacks against the browser, database stealing and backdoor placement
XSS Reverse Shell. Session hijacking by tunnelling HTTP over HTTP using HTML5 Cross Origin Requests
SSL-TLS Security checker. Scanner to discover vulnerabilities in SSL and TLS installations
SAP Testing. It can detect Hostnames, SAPSID and System Number from SAP Error messages. It can find all ICF Public and Private Services (like Info Service, SOAP RFC) and Web Services (like SAP Start Service) that respond to a Request 200 OK. If login is Basic Authentication, it launches a Brute Force Attack and Verb Tampering. It automatically checks all HTTP(S) ports and finds interesting pages, including Admin pages and, using WAM, it would try to login to the system with different users in REMOTE_USER header
SCADA Testing. It provides Vulnerability detection capabilities for multiple SCADA Master Systems
WiFi Testing. WiFi Routers Vulnerability Scanner
Team Reviewer, ThreadFix and OWASP Defect Dojo integration modules. Vulnerabilities found will be correlated to third party scanners
GHDB-ExploitDB. Google Hacking DB integrated in Exploit-DB is used to check if the web application has a publicly available exploit
Deep Discovery. Automatic Discovery and Exploit of main DBMS, AS, CMS, DMS, Wiki and e-Commerce platforms, like: Wordpress, Drupal, ccPortal, WebGui, Rubedo, EzPublish, MODX, Concrete, X3, PHPNuke, DotNetNuke, Orchad, Joomla, Umbraco, Seed, Magento, OpenCart, WebSphere Commerce, WebSphere Portal, MediaWiki, Movable Type, phpLiteAdmin, TWiki, SharePoint, Documentum, FileNet, OWS, BI Publisher, Splunk, LiteSpeed, PeopleSoft, Siebel, Alfresco, Nuxeo, iPlanet, GlassFish, phpBB, Magnolia, ZenCart, Tableau, ZenCart, Hesk, IBM Tivoli EP and WebSphere AS. Fingerprint the web server type and version. Report old versions of server software if it contains known vulnerabilities. Discover web server configuration problems (directory listing, backup files, old configuration files, etc.). Identify specific web applications that are running on the web server. Check for known application vulnerabilities
DISCLAIMER: Due we make use of opensource components (IronWasp by ANANT SHRIVASTAVA and DISCLAIMER: Due we make use of opensource components (Arachni Web UI by Tasos Laskos), we do not sell the product, but we offer a yearly subscription-based Commercial Support to selected Customers.
COPYRIGHT (C) 2014-2022 SECURITY REVIEWER SRL. ALL RIGHTS RESERVED.