Firmware Reviewer Cloud Service provides in-depth firmware analysis (binaries, file systems, containers, virtual machines, IoT, UEFI, Appliances, Network Devices, Smart Meters, Surveillance devices, Drones, etc.), allowing to explore vulnerabilities at the same time to keeping the software securely in your own hands, for your eyes only. It can be used for a bunch of binary file formats, withNo need of related physical device. Further, we offer a Firmware Image Check certification.
...
It is available in Cloud. For further explanation, please take a look to FAQ section.
Main Topics
| Table of Contents |
|---|
...
System Requirements
Firmware Reviewer offers a Cloud platform for Analyzing and continuously Monitoring your Firmware images.
Accelerate digital transformation with comprehensive security across your IoT/OT infrastructure.
In-depth Firmware analysis, Secured Dashboard, Compliance Reporting
Full visibility into assets and risk across your entire IoT/OT environment
Continuous monitoring for threats and vulnerabilities, with IoT/OT-aware behavioral analytics and threat intelligence with integrated alerting system
Interoperability with SIEM/SOAR and XDR platforms to stop attacks with automated, cross-domain security
Architecture
Firmware Reviewer, further to its own engine, makes use of other well-known platforms, like FACT (Firmware Analysis Comparison Tool), Intel ME Analyzer, RedBoot, FirmWalker, Firmware Modification Kit, angr, Radare, Firmware Analysis Tool, Firmadyne, ByteSweep,Karonte,FWAnalyzer,Ghidra,FIT, IoTSecFuzz, EXPLioT, CapStone Framework and Binwalk engines to analyze and compare different versions against vendor's databases, Karonte Dataset and Fraunhofer Institute database. Analysis are normalized and correlated, presenting a unique dashboard. This is possible through our Plugin Infrastructure.is a Cloud service accessible via Internet through a Standard Browser. Latest versions of Edge Chromium, Google Chrome and Mozilla FireFox are supported.
Optionally, you can use our Client App for analyzing your Firmware Image locally.
Minimum RAM: 4GB (8GB is recommended)
CPU Cores: 2 (4 is recommended)
Free Disk Space: the minimum required by your browser. In case the Client App is used you need triple the size of your Firmware Image available on your disk.
Main Topics
| Table of Contents |
|---|
Service
Firmware Reviewer offers a Cloud platform for Analyzing and continuously Monitoring your Firmware images.
Accelerate digital transformation with comprehensive security across your IoT/OT infrastructure. 98
...
Firmware Reviewer shares FACT (Firmware Analysis Comparison Tool) architecture, adding a lot of new features. Respect than FACT, it is more flexible on hardware configuration, while enhancing performances 12x.
...
Keep your Firmware Secured
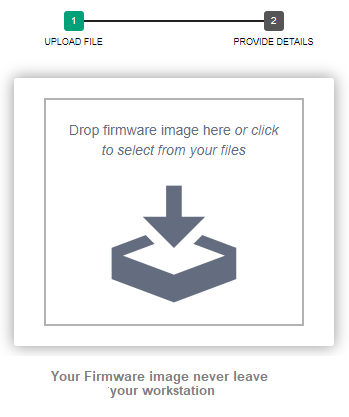
Your Firmware images won’t be uploaded to the internet.
...
...
...
A Client App (Firmware Reviewer Submit Interface) is optionally available, enabling teams to scan locally. Registered Customers simply use this App for retrieving image’s relevant information and send it encrypted to Firmware Reviewer engine.
Using this App:
Firmware images won’t be uploaded to the internet
Firmware images never leave your workstation.
Firmware Analysis' Results and Reports will be stored and downloaded using AES-256 encryption.
Nor the Cloud server administrator can access the results and reports.
The encryption key is known only by you only.
Compliance
Firmware Reviewer provides Reports compliant to:
...
7z, ace, apk, ar, arj, bzip2, CAB, cpio, deb, dmg, gzip, hex, ice, ipa, ISO9660, lha, lz4, lzip, LZMA, lzo,, mpkg, pkg, SFX, SREC, SY_, rar, rpm, rzip, SIT, SQX, tar, TBZ, xar, xapk, xz, zip, zlib, zstd
from the following vendors:
...
The OWASP Firmware Security Testing Methodology is composed of nine stages tailored to enable security researchers, software developers, consultants, hobbyists, and Information Security professionals with conducting firmware security assessments. Firmware analysis is a tough challenge with a lot of tasks. Many of these tasks can be automated (either with new approaches or incorporation of existing tools) so that a security analyst can focus on its main task: Analyzing the firmware (and finding vulnerabilities). Firmware Reviewer implements this automation leading to more complete analysis as well as a massive speedup in vulnerability hunting and is able to assist you during all the nine stages:
...
Comparison between Versions
The File Compare check is a mechanism to compare a file from a previous run with the file from the current run. It provides more insights into file changes, since it allows comparing two versions of a file rather than comparing only a digest. Last, the Tree Check will produce an informational output listing new files, deleted files, and modified files. Firmware Reviewer can compare several images or single files. Furthermore, Unpacking, analysis and compares are based on plug-ins guaranteeing maximal flexibility and expandability.
...
In many cases you might want to compare Firmware samples. For instance, you might want to know if and where a manufacturer fixed an issue in a new firmware version. Or you might want to know if the firmware on your device the original firmware is of provided by the manufacturer. If they differ, you want to know which parts are changed for further investigation. Again, Firmware Reviewer is able to automate many of these challenges, like: Identify changed / equal files and Identify changed software versions.
...
DISCLAIMER: Firmware Reviewer never operates on physical devices. Security Reviewer declines all responsabilities derived by inappropriate use of Firmware Reviewer software.
COPYRIGHT (C) 2014-2022 SECURITY REVIEWER SRL. ALL RIGHTS RESERVED.