| Table of Contents |
|---|
...
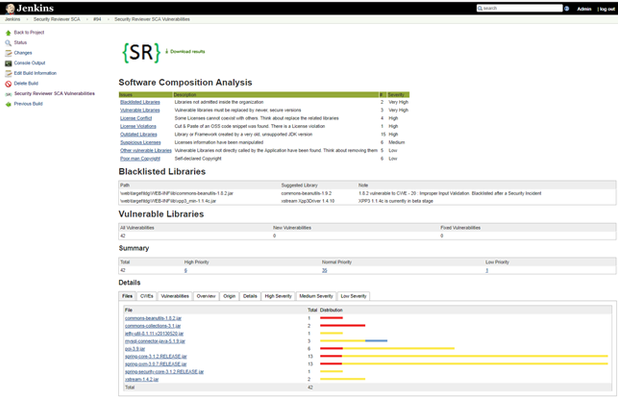
Software Composition Analysis Jenkins and Bamboo native plugins and CLI Interface (test on many CI/CD platforms) provide a 360 degrees solution covering all your DevOps needs. 3rd-party libraries can be analyzed (Open Source Analysis-OSA) using a shared folder located on Network File System (NFS), a Nexus Repository or JFrog Artifactory for discovering Vulnerable Libraries, Vulnerable Frameworks, Blacklisted/ Discontinued/ Outdated / Obsolete/ Deprecated libraries and frameworks. Legal issues like: Blacklisted Licenses, Licenses Conflict, No-licensed libraries, Suspicious (modified) licenses and Poor-man Copyrights are fully-detected from the tool.
...
Analyzer | File Types Scanned | Analysis Method |
SRslic ** | ASP, ASPX, HTML, JSP, JSF, JAVA, C#, VB.NET, C, CPP, H, HPP, M, MM, SWIFT, PHP, JS, TS, RB, GROOVY, GY, PY, PERL, PL, SCALA, GO, R, KT, CLJ, ERL, SH, PS1, AU3, LUA, XML files | Reveals Licenses in Whitelist, Licenses in Blacklist, License Conflicts, Suspicious Licenses, License Violations and Poor’s man copyrights found in source code. |
Artifactory | jFrog Artifactory | Analyzer which will attempt to locate a dependency on a jFrog Artifactory service by SHA-1 digest of the dependency. |
Archive | Zip archive format (*.zip, *.ear, *.war, *.jar, *.sar, *.apk, *.nupkg); Tape Archive Format (*.tar); Gzip format (*.gz, *.tgz); Bzip2 format (*.bz2, *.tbz2) | Extracts archive contents, then scans contents with all available analyzers. |
Assembly | .NET Assemblies (*.exe, *.dll) | Uses GrokAssembly.exe, which requires .NET Framework or Mono runtime to be installed, otherwise .NET Assemblies will be analyzed by FileInfo and NuSpec analyzers only. |
Packrat | CRAN | packrat.lock files (R language). |
RetireJS | JavaScript | It uses the manually curated list of vulnerabilities from the RetireJS community along with the necessary information to assist in identifying vulnerable components. Vulnerabilities documented by the RetireJS community usually originate from other sources such as the NVD, OSVDB, NSP, and various issue trackers. |
| Apache Ivy | Ivy is a dependency manager | Scans dependencies n ivy Ant extension |
CMake | CMake project files (CMakeLists.txt) and scripts (*.cmake) | Regex scan for project initialization and version setting commands. |
MSBuild | .NET Assembly | Analyzes MSBuild Projects |
MavenGradleAnt | Analyze Maven, Ant and Gradle build files for Java | Analyze pom.xml, build.gradle, and build.xml. |
GoDep | Analyze GitHub dependency files for GO Language, .go | Analyze vendor.conf, godeps.json, godeps.json gomod files, and gopkg.toml. |
| Distroless Images | Google Distroless Images | They contain only your application and its runtime dependencies |
Jar Analyzer | Java archive files (*.jar); Web application archive (*.war) | Examines archive manifest metadata, and Maven Project Object Model files (pom.xml). |
NSP | Node Security Project is used to analyze Node.js’ package.json files for known vulnerable packages. | Recently acquired by NPM inc., this service will be still available until September, 30. |
| SNYK | JavaScript, .NET, Java, TypeScript, Python, Ruby, Scala, GO | Scans scripts and dependencies |
Nuspec | Nuget package specification file (*.nuspec) | Uses XPath to parse specification XML. Analyze also packages.config and (*proj or sln), project.lock.json and project.assets.json or PackageReference. |
OpenSSL | OpenSSL Version Source Header File (opensslv.h) | Regex parse of the OPENSSL_VERSION_NUMBER macro definition. |
Ruby bundler‑audit | Ruby Gemfile.lock files | Executes bundle-audit and incorporates the results into the dependency-check report. |
Autoconf | Autoconf project configuration files (configure, configure.in, configure.ac) | Regex scan for AC_INIT metadata, including in generated configuration script. |
CocoaPods | CocoaPods .podspec and podfile.lock files | Extracts dependency information from specification file and lock file, for Objective-C and SWIFT projects. |
Composer Lock | PHP Composer and PHP Pear | Parses PHP Pear package.xml, PHP Composer lock and composer.json files for exact versions and dependencies. |
Node.js | NPM package specification files (package.json) | Parse JSON format for metadata. |
Python Metadata | Python source files (*.py); Package metadata files (PKG-INFO, METADATA); Package Distribution Files (*.whl, *.egg, *.zip) Anaconda and environment.yml | Regex scan of Python source files for setup tools metadata; Parse RFC822 header format for metadata in all other artifacts. Also scans dependencies in yml files. |
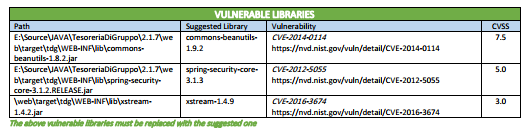
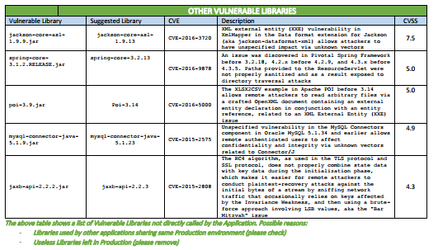
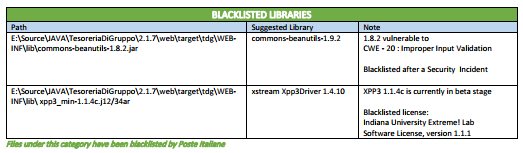
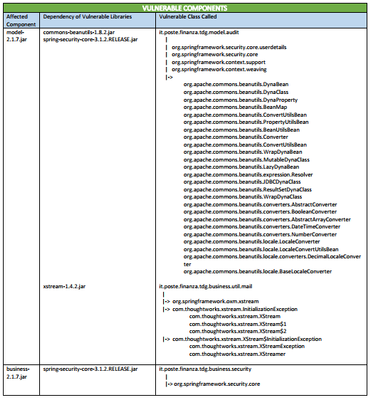
FileInfo-JarManifest** | jar, war, ear, dll, exe, lib, shared libs and machOS, UPX, PE executables | Reveals Blacklisted Libraries, Outdated Libraries, Other Vulnerable Libraries. |
Ruby Gemspec | Ruby makefiles (Rakefile); Ruby Gemspec files (*.gemspec) | Regex scan Gemspec initialization blocks, Rakefile and gemfile.lock for metadata. |
SWIFT | SWIFT Package Manager’s Package.swift | Extracts dependency information from swift package file. |
**awesome-C, awesome-CPP, cppreference, awesome-dotnet, awesome-javascript, awesome-typescript, SwifterSwift, Three20, PyPi, awesome-scala | Fresh updated lists of best (awesome) libraries, packages and frameworks, specialized for each Programming language | Seeks for new and updated libraries, packages and frameworks coming directly from programmer’s community. |
SBT | SCALA | Scans build.sbt for dependencies. |
| CRAN | R | Scans for add-on packages from CRAN |
| Akku.scm | R | Scans a Scheme from Akku.scm |
CPAN | Perl | Analyze dependencies in Makefile.PL. |
| Leiningen | Clojure | Scans Lein scripts |
| LuaRocks | LUA | Scans rocks packages |
ERL | Erlang HEX | Analyze dependencies in rebar.config. |
| Rust | Rust | Scans cargo.toml file |
| au3pm | Auto-IT | Scans json.au3 |
| Alpine | Alpine Linux package keeper (manager) | Scans signed tar.gz archives containing programs, configuration files, and dependency metadata |
| Debian | Debian Package Manager | Scan .deb packages |
| RPM | Red Hat Package Manager | Scan .rpm files |
| Bower | JavaScript | Scans bower.json |
| Chocolatey | Windows Packages | Scans c4b files |
| Clojars | Clojure | Scans Lein scripts and Cloure JAR files |
| Conan, IAR | C/C++ | Scans makefile and .dep file |
**Security Reviewer’s SCA unique features
Package Managers
SCA supports several Package Managers.
...
...
...
The most significant effort with any OSS audit is inventorying existing use of OSS components. That inventory can occur manually by interviewing each developer and asking them to identify the OSS components they have downloaded and used in the development process. For long standing development teams that have never been through this exercise, that can be a difficult, if not impossible, task. While it may be easy to remember OSS components that were recently incorporated into a development project, that may not be true for software developed years ago. Alternatively, third party software products exist that can automate the inventory process.
I It support the following SBOM standards:
Security Reviewer – Composition Analysis module can scan your software code and, using sophisticated pattern matching algorithms, identify the various OSS components present in your software code. While some vendors require that source code be uploaded to their cloud environment for processing, Security Reviewer can operate entirely on-premises and using hashed values of the source code to avoid the risk of source code disclosure outside the enterprise. Unless an enterprise is in the early stages of its development process or has kept an accurate running list of OSS components, the automated process will be far more accurate and complete. Further, in more and more significant financing and M&A transactions, the investors or acquirers themselves are using such automated tools as part of the due diligence process, so to simply assume that the manual inventory process will be “good enough” may be misguided. Representing compliance and possession of an accurate list of OSS components, only to later find out from a counterparty using an automated tool that this is not the case, can be just as bad, if not worse, than not having completed an audit at all.
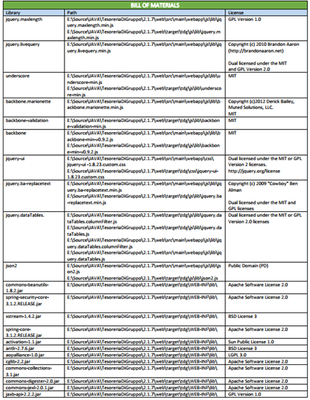
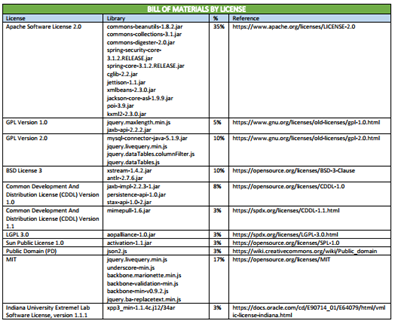
OSS License Inventory
Whether done manually or via an automated process, the first step is to complete an accurate and complete inventory of each OSS component present in the software. Next, one must identify the license type associated with each OSS component. If the inventory was done manually, then this will require a search of the source website of each OSS component to determine the applicable license type. If the inventory was automated, Security Reviewer automated tool identifies the license type for you, based on its extensive database of OSS components. While there are hundreds of different OSS license types, most OSS inventories tend to consist of only a few dozen license types.
- Use Characteristics Inventory
- Next, for certain OSS license types, the enterprise must determine how the OSS component is used.
These use characteristics typically include:
...
-- Debian Security https://security-tracker.debian.org
-- Linux Security https://linuxsecurity.com/
-- RedHat Security https://access.redhat.com/security
-- Oracle Security Advisory https://www.oracle.com/technetwork/security-advisory
-- SuSe OVAL Descriptions https://www.suse.com/support/security/oval/
-- Ubuntu CVE Tracker https://people.canonical.com/~ubuntu-security/cve/main.html
-- Alpine Linux Security https://alpinelinux.org
-- CentOS Security https://www.centosblog.com/categories/security/
-- Microsoft Security Response Center https://portal.msrc.microsoft.com/en-us/security-guidance
-- OSS Index by Sonatype: https://ossindex.sonatype.org/
-- NVD by NIST: https://www.nist.gov/programs-projects/national-vulnerability-database-nvd
-- VulnDB: https://vuldb.com/
-- Maven Central: https://mvnrepository.com/repos/central (Java, Scala, Kotlin)
-- NuGet Packages: https://www.nuget.org/packages (.NET)
-- PyPy compatibility: https://bitbucket.org/pypy/compatibility/wiki/Home (Python)
-- Common Weakness Enumeration (CWE): http://cwe.mitre.org/
-- CVE Details: https://www.cvedetails.com/
...