| Table of Contents |
|---|
Many applications incorporate external open source and third-party components that enable developers to build new functionality quickly and efficiently. But while the use of open source components has many benefits, it also introduces risk.
...
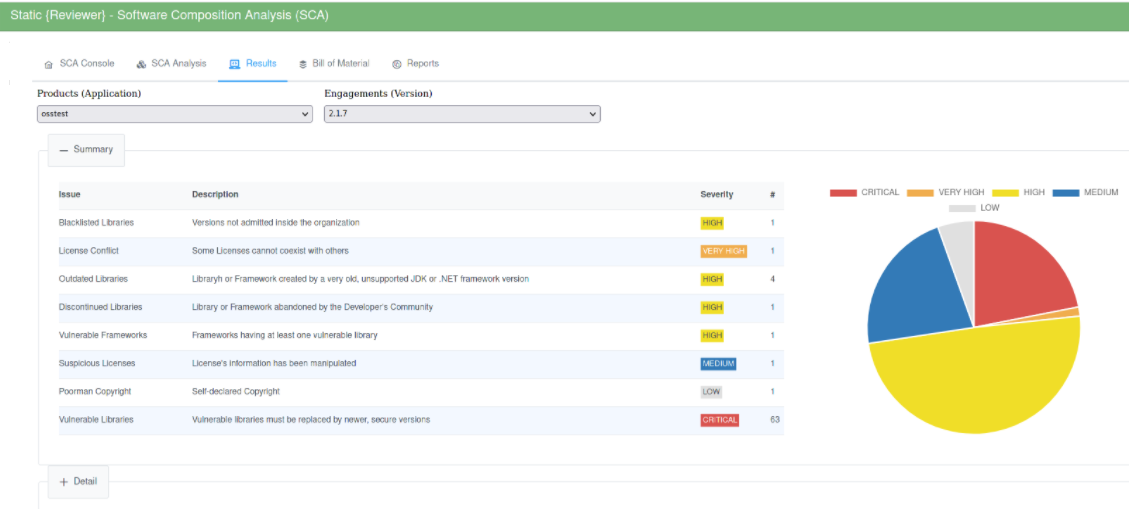
Web App
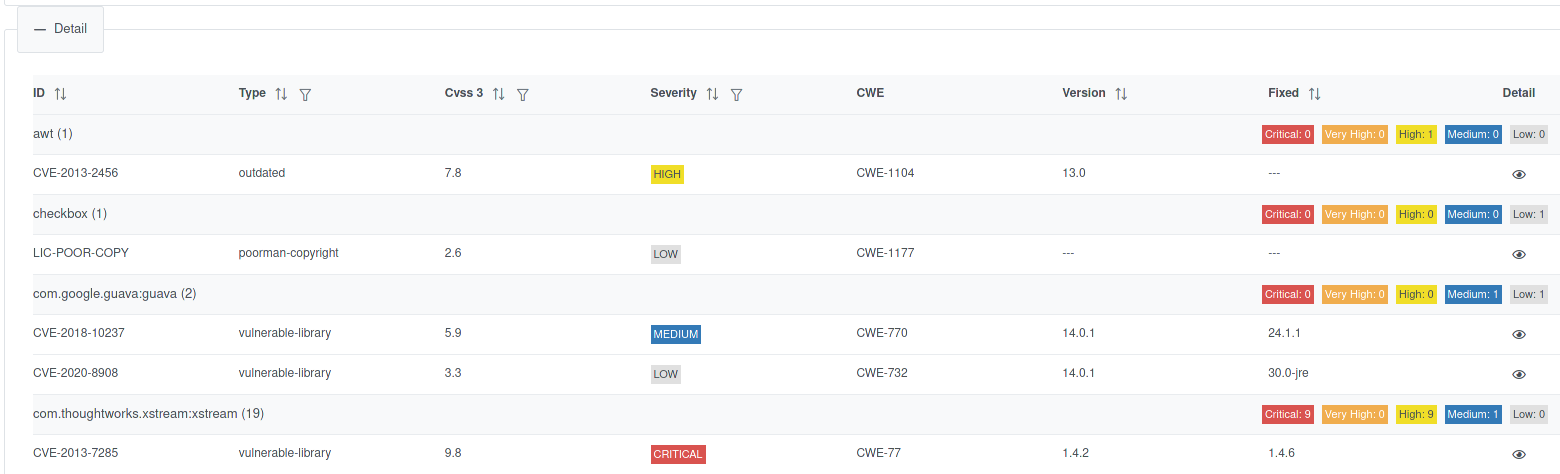
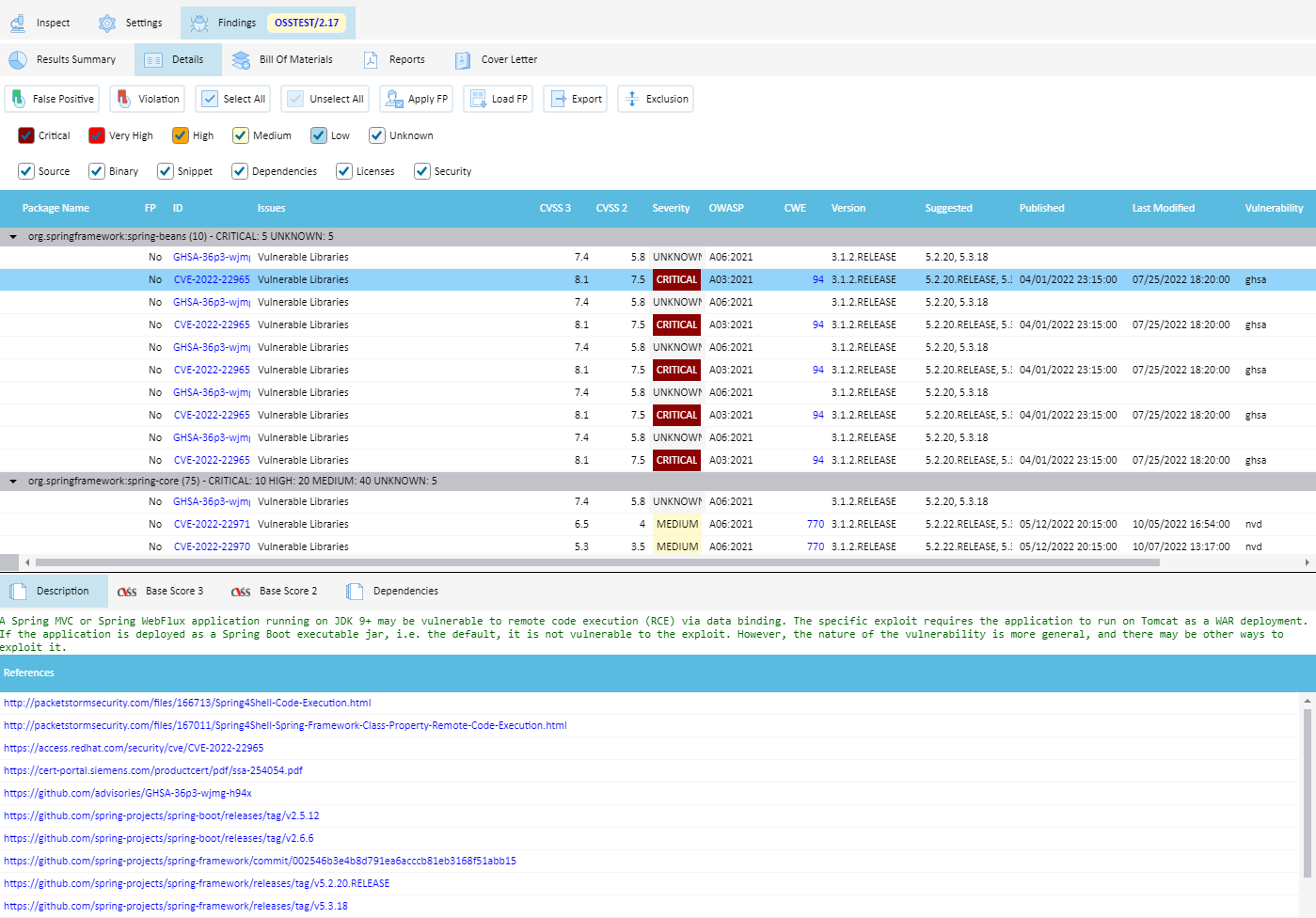
You can view details:
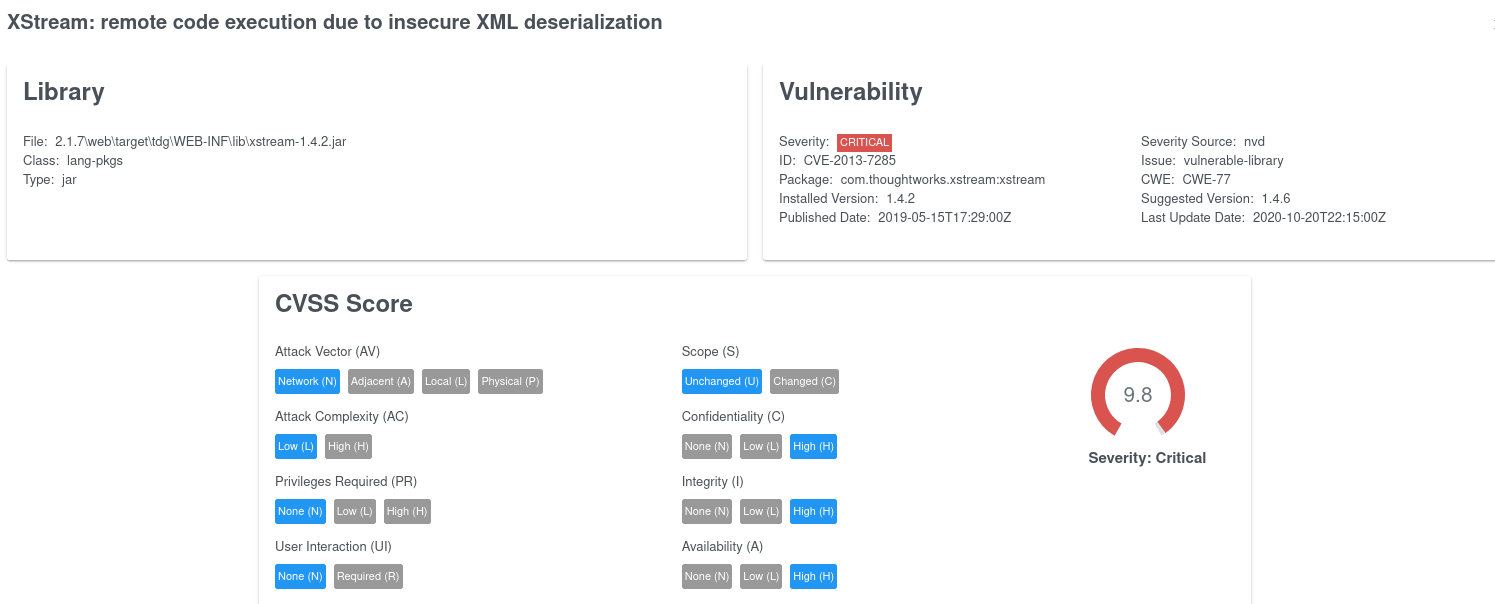
And drill-down to the single issue, a Fixed version is also suggested:
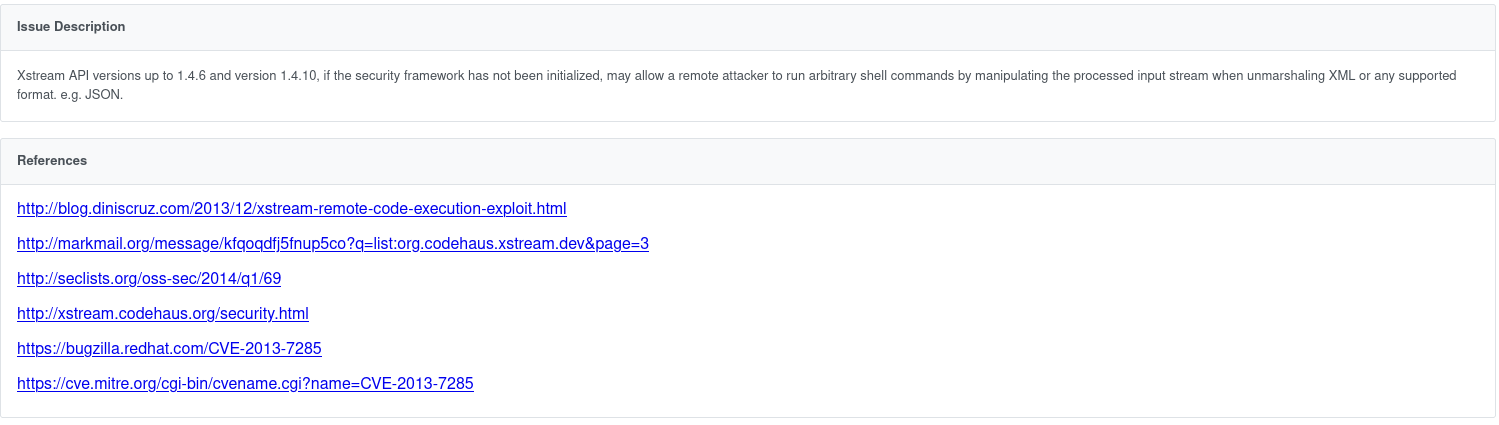
including all References and Exploits:
SCA Desktop
And drill-down to the single issue, a Fixed version is also suggested:
including all References and Exploits:
SCA Desktop
Application Architecture
SCA Reviewer is able to create a Design Structure Matrix (DSM) by reading the compiled code (JAR, DLL binaries) and/or related UML diagrams.
DSM-Design Structure Matrix
An example of SCA Reviewer’s automatically generated Design Structure Matrix is shown below:
A Design Structure Matrix consists of a matrix to visualize Dependencies of hierarchically organized elements and a set of algorithms which can be applied on the matrix to sort the elements in order to discover layering.
A Design Structure Matrix (DSM) is made by two parts
A matrix to visualize dependencies
Algorithms which can be applied on the matrix to discover e.g. layering in the software.
The DSM consists of a matrix with the same elements in the rows and columns
The hierarchy of packages and elements is visible on the left.
The relations between the elements are shown in the cells.
In a DSM, the hierarchy can also be folded in whole or in part. The relational strengths of the collapsed cells are simply combined. As a result, the DSM will become more compact, but will still remain correct in terms of content.
In this way it is possible to display a system with thousands of elements and still keep the overview.
DSM Architectural Discovery
By applying a partitioning algorithm on the DSM, the layering of the software will be discovered by SCA Reviewer during the binary analysis. Such an algorithm tries to reorder the DSM in such a way that as many relationships as possible come under the diagonal.
After partioning elements with many inbound relationships (providers) have shifted to the bottom, while the elements with many outgoing relationships (consumers) have shifted to the top.
Cyclic relations can be easily spotted, because the type of relations remain above the diagonal.
DSM Assist in refactoring (Desktop only)
A DSM can be used to improve the dependency structure. One can think of:
Removing cyclic dependencies.
Improving the cohesiveness of a component by move elements to other component were the have stronger relations.
In the matrix we can move an element to another component or layer, combine it with other elements or split and then recalculate all dependencies to see if this yields a better dependency structure.
After recalculating the dependencies it can be seen that the cyclical relationship between the presentation and application layer has disappeared.
The advantages of such an impact analysis are particularly evident in improvement scenarios that take place at the architectural level and thus affect multiple components. Without the use of a DSM, such analysis are unreliable, because the intended and the actual software architecture often do not match.
DSM-Supported Languages
.NET: C# and vb.NET Assembly
JAVA, Clojure, Groovy, Kotlin JAR files
C/C++ Source and Header files
UML in Sparx System Enterprise Architect format
DSM Files from 3rd-party tools (for example ArgoUML)
DSI Model. Two DSI Model files can be compared
A DSI Model file is a way to import 3rd-party analyzer’s DSM output to SCA Reviewer.. A DSI file represent an analyzer’s output. Each code analyzer must export its DSM results to DSI file. To ensure that the SCA Reviewer can import this file, it must conform the DSI file XSD schema below:
CI/CD plugin
Software Composition Analysis Jenkins and Bamboo native plugins and CLI Interface (test on many CI/CD platforms) provide a 360 degrees solution covering all your DevOps needs. 3rd-party libraries can be analyzed (Open Source Analysis-OSA) using a shared folder located on Network File System (NFS), a Nexus Repository or JFrog Artifactory for discovering Vulnerable Libraries, Vulnerable Frameworks, Blacklisted/ Discontinued/ Outdated / Obsolete/ Deprecated libraries and frameworks. Legal issues like: Blacklisted Licenses, Licenses Conflict, No-licensed libraries, Suspicious (modified) licenses and Poor-man Copyrights are fully-detected from the tool.
...
Analyzer | File Types Scanned | Analysis Method |
SRslic ** | ASP, ASPX, HTML, JSP, JSF, JAVA, C#, VB.NET, C, CPP, H, HPP, M, MM, SWIFT, PHP, JS, TS, RB, GROOVY, GY, PY, PERL, PL, SCALA, GO, R, KT, CLJ, ERL, SH, PS1, AU3, LUA, XML files | Reveals Licenses in Whitelist, Licenses in Blacklist, License Conflicts, Suspicious Licenses, License Violations and Poor’s man copyrights found in source code. |
Artifactory | jFrog Artifactory | Analyzer which will attempt to locate a dependency on a jFrog Artifactory service by SHA-1 digest of the dependency. |
Archive | Zip archive format (*.zip, *.ear, *.war, *.jar, *.sar, *.apk, *.nupkg); Tape Archive Format (*.tar); Gzip format (*.gz, *.tgz); Bzip2 format (*.bz2, *.tbz2) | Extracts archive contents, then scans contents with all available analyzers. |
Assembly | .NET Assemblies (*.exe, *.dll) | Uses GrokAssembly.exe, which requires .NET Framework or Mono runtime to be installed, otherwise .NET Assemblies will be analyzed by FileInfo and NuSpec analyzers only. |
Packrat | CRAN | packrat.lock files (R language). |
RetireJS | JavaScript | It uses the manually curated list of vulnerabilities from the RetireJS community along with the necessary information to assist in identifying vulnerable components. Vulnerabilities documented by the RetireJS community usually originate from other sources such as the NVD, OSVDB, NSP, and various issue trackers. |
| Apache Ivy | Ivy is a dependency manager | Scans dependencies n ivy Ant extension |
CMake | CMake project files (CMakeLists.txt) and scripts (*.cmake) | Regex scan for project initialization and version setting commands. |
MSBuild | .NET Assembly | Analyzes MSBuild Projects |
MavenGradleAnt | Analyze Maven, Ant and Gradle build files for Java | Analyze pom.xml, build.gradle, and build.xml. |
GoDep | Analyze GitHub dependency files for GO Language, .go | Analyze vendor.conf, godeps.json, godeps.json gomod files, and gopkg.toml. |
| Distroless Images | Google Distroless Images | They contain only your application and its runtime dependencies |
Jar Analyzer | Java archive files (*.jar); Web application archive (*.war) | Examines archive manifest metadata, and Maven Project Object Model files (pom.xml). |
NSP | Node Security Project is used to analyze Node.js’ package.json files for known vulnerable packages. | Recently acquired by NPM inc., this service will be still available until September, 30. |
| SNYK | JavaScript, .NET, Java, TypeScript, Python, Ruby, Scala, GO | Scans scripts and dependencies |
Nuspec | Nuget package specification file (*.nuspec) | Uses XPath to parse specification XML. Analyze also packages.config and (*proj or sln), project.lock.json and project.assets.json or PackageReference. |
OpenSSL | OpenSSL Version Source Header File (opensslv.h) | Regex parse of the OPENSSL_VERSION_NUMBER macro definition. |
Ruby bundler‑audit | Ruby Gemfile.lock files | Executes bundle-audit and incorporates the results into the dependency-check report. |
Autoconf | Autoconf project configuration files (configure, configure.in, configure.ac) | Regex scan for AC_INIT metadata, including in generated configuration script. |
CocoaPods | CocoaPods .podspec and podfile.lock files | Extracts dependency information from specification file and lock file, for Objective-C and SWIFT projects. |
Composer Lock | PHP Composer and PHP Pear | Parses PHP Pear package.xml, PHP Composer lock and composer.json files for exact versions and dependencies. |
Node.js | NPM package specification files (package.json) | Parse JSON format for metadata. |
Python Metadata | Python source files (*.py); Package metadata files (PKG-INFO, METADATA); Package Distribution Files (*.whl, *.egg, *.zip) Anaconda and environment.yml | Regex scan of Python source files for setup tools metadata; Parse RFC822 header format for metadata in all other artifacts. Also scans dependencies in yml files. |
FileInfo-JarManifest** | jar, war, ear, dll, exe, lib, shared libs and machOS, UPX, PE executables | Reveals Blacklisted Libraries, Outdated Libraries, Other Vulnerable Libraries. |
Ruby Gemspec | Ruby makefiles (Rakefile); Ruby Gemspec files (*.gemspec) | Regex scan Gemspec initialization blocks, Rakefile and gemfile.lock for metadata. |
SWIFT | SWIFT Package Manager’s Package.swift | Extracts dependency information from swift package file. |
**awesome-C, awesome-CPP, cppreference, awesome-dotnet, awesome-javascript, awesome-typescript, SwifterSwift, Three20, PyPi, awesome-scala | Fresh updated lists of best (awesome) libraries, packages and frameworks, specialized for each Programming language | Seeks for new and updated libraries, packages and frameworks coming directly from programmer’s community. |
SBT | SCALA | Scans build.sbt for dependencies. |
| CRAN | R | Scans for add-on packages from CRAN |
| Akku.scm | R | Scans a Scheme from Akku.scm |
CPAN | Perl | Analyze dependencies in Makefile.PL. |
| Leiningen | Clojure | Scans Lein scripts |
| LuaRocks | LUA | Scans rocks packages |
ERL | Erlang HEX | Analyze dependencies in rebar.config. |
| Rust | Rust | Scans cargo.toml file |
| au3pm | Auto-IT | Scans json.au3 |
| Alpine | Alpine Linux package keeper (manager) | Scans signed tar.gz archives containing programs, configuration files, and dependency metadata |
| Debian | Debian Package Manager | Scan .deb packages |
| RPM | Red Hat Package Manager | Scan .rpm files |
| Bower | JavaScript | Scans bower.json |
| Chocolatey | Windows Packages | Scans c4b files |
| Clojars | Clojure | Scans Lein scripts and Cloure JAR files |
| Conan, IAR | C/C++ | Scans makefile and .dep file |
**Security Reviewer’s SCA unique features
Package Managers
SCA supports several Package Managers.
...
-- Debian Security https://security-tracker.debian.org
-- Linux Security https://linuxsecurity.com/
-- RedHat Security https://access.redhat.com/security
-- Oracle Security Advisory https://www.oracle.com/technetwork/security-advisory
-- SuSe OVAL Descriptions https://www.suse.com/support/security/oval/
-- Ubuntu CVE Tracker https://people.canonical.com/~ubuntu-security/cve/main.html
-- Alpine Linux Security https://alpinelinux.org
-- CentOS Security https://www.centosblog.com/categories/security/
-- Microsoft Security Response Center https://portal.msrc.microsoft.com/en-us/security-guidance
-- OSS Index by Sonatype: https://ossindex.sonatype.org/
-- NVD by NIST: https://www.nist.gov/programs-projects/national-vulnerability-database-nvd
-- VulnDB: https://vuldb.com/
-- Maven Central: https://mvnrepository.com/repos/central (Java, Scala, Kotlin)
...