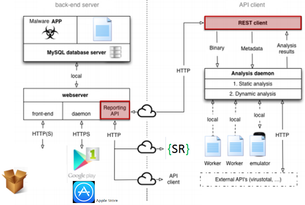
Mobile Reviewer is a worldwide brand of Security Reviewer offered on demand for Mobile Apps Inspection. A robust, cloud infrastructure is behind this offer.
It provides:
Mobile Code Inspection
The following languages are supported:
Android
Android JAVA
Kotlin
Android C++ SDK
With support of:
Unity
Corona SDK
Xamarin
Titanium
TheAppBuilder
PhoneGap
NativeScript
Ionic
Sencha Touch
React Native
JQuery Mobile
Sproutcore
Flutter
Cordova
iOS
iOS Objective-C and Objective-C++
iOS Swift
With support of:
Appium
Earlgrey
OCMock
Detox
XCTest and XCUITest
Further iOS libraries we support: https://github.com/vsouza/awesome-ios
Hybrid Analysis
Mobile Reviewer is built on the software-as-a-service (SaaS) model, enabling enterprises to get on-demand security assessments of their Mobile Apps. Mobile security assessment software can be expensive to purchase, and it needs constant upgrades to keep up with ever-evolving threats. Today's corporate security groups are not staffed to handle the specialized skills needed to perform code analysis and security testing.
Mobile Reviewer frees enterprises from having to spend resources on the purchase of software or Mobile device simulators, on hiring software security experts and consultants to operate it, and on constant maintenance to keep effective. With Mobile Reviewer, enterprises simply submit Apps through an online platform and quickly get back test results.
Mobile Reviewer is easy to use and access, allowing enterprises to roll out Mobile security quickly and efficiently.
Mobile Reviewer now supports Static and Dynamic Analysis of both Android and iOS apps. Reviewing Mobile Apps is time-consuming and difficult to make routine. Adopting an online Mobile scanning service can save time by focusing human involvement on reviewing potential risks and enhancing system stability with more accurate and usable results.
Mobile Reviewer will do it for you. To perform the audit we rely on the expertise of a dedicated staff from 2 to 5 auditors per Mobile App, and we based the analysis on the following test plan:
App enhanced decompiling: We use a combination of technologies for decompiling and extracting configuration files from the App. Further we have our own code enrichment methodology, especially useful when code has been obfuscated. This phase provides: seeking for unwanted additional code-variables-objects-parameters, executing decompiled code static analysis, comparing respect than original source code (when available).
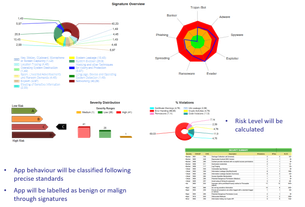
Permission analysis (Android): To make smartphone users aware of the personal information an App might access, the Android operating system requires users to review and grant a set of permissions for the App to function. Android Apps must declare permissions for nearly everything, from controlling vibration, Internet access, and writing to the SD card, to monitoring your location and sending SMS messages. However, research demonstrates that few users are well equipped to evaluate the set of permissions requested by Apps, hence permissions are often ignored even though they might appear irrelevant to the proper function of the app. We studied 500K+ apps, roughly 88% of 20+ Android marketplaces and we are able to recognize applications which might pose privacy risks and that this represents a large number of available applications (46% of the Apps collected). To distinguish between low/no risk applications and those that have the potential to release sensitive data, we adopted a quantitative metric for characterizing Apps, called Sensitivity Score.
Virus-Malware analysis: validates the use of potentially dangerous code itself; that is, calls to vulnerable functions and procedures. Part of the analysis is done with 50+ antiviruses, and part recognizing malware patterns inside the code.
Screenshots capture: Capturing screenshots from running Apps is not only a graphical issue; it is also a demonstration of different running phases that has been solicited from our tests. Using our patented Dynamic Image Interpreter, Mobile Reviewer detects Async Inputs, Application Status Changes, Lost Connections, Unhandled Errors and Ransomware by interpreting the images dynamically.
Information Leakage. Lists all tainted information during Apps execution, like IMEI, personal data, e-mail, external IP and DNS access, File access, Hardcoded URL and URI, Encryption keys, phone calls, SMS/MMS sent, etc.
Structural analysis: detects problems due to incorrect decisions in the organization of code.
Dead Code analysis: seeking for unused and/or unitialized code, variable, object and parameters that can be manipulated for hiding dangerous code.
Fingerprint analysis: detects all vulnerable libraries and frameworks used by the application.
Certificates analysis: detects all invalid certificates used by the application.
Encryption analysis: detects all invalid or weak encryption used by the application.
Configuration files analysis: correspondence checks b/w code and configuration files; seeking for dangerous configuration tags; unsecured cookies, environment variables, library and framework configuration, insecure authorizations and authentication; misconfiguration of application logic and data flows, code injection exposure.
Exception handling and Logging robustness check.
Android Hardcoded Secrets: Rooted phone, Hard disk forensics, adb backup, Debuggable application allowing run-as (mitigated by Android). Social engineering, Bug in application allowing for data exfiltration, Bug in application allowing arbitrary command execution (not mitigated by Android).
Apple iOS Key Security Flaws: Limited benefit of encryption for powered-on devices, Evidence of past hardware (SEP) compromise, Limitations of “end-to-end encrypted” cloud services.
iOS IPA and APK/XAPK binary analysis: .ipa and .apk files are just zipped files that include the application executable and a bunch of other stuff. In most cases they are not 100% encrypted and contains images, web pages, db files, configuration files and even zipped source code.
Protocol testing: Find in the code references to security protocols, execute Dynamic Analysis of TLS/SSL Security, SSL Pinning Bypass, LGTM issues, and REST API exposed for TLS/SSL included.
Intent/app extension dumper: Through auxiliary Frida or Needle script.
Correlation: Static and Dynamic analyses will be correlated using Dynamic Syntax Tree, combining, and correlating the results. You are able to identify which vulnerabilities are truly exploitable and should be at the top of your remediation list.
These checks are first performed by automated procedures, then manual intervention will needed, taking into account the established risk on the application.
Attackers can potentially use many different paths through your application to do harm to your business or organization. Each of these paths represents a risk that may, or may not, be serious enough to warrant attention.
For further explanation, please see our Scientific Article.
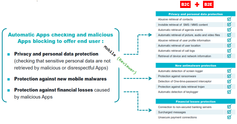
Key Business Benefits
Identify and mitigate risk posed by all attackers, including malicious advertising, to eliminate potential attacks that could affect the "brand" image of your company in the marketplace.
Decreased overall cost by identifying larger number of vulnerabilities
Decrease risk by applying a unique methodology aimed at identifying deeply-rooted, major impact vulnerabilities that go undetected with other approaches.
Improved compliance with regulations and control frameworks, such as the OWASP Top Ten Mobile 2016, Payment Card Industry Data Security Standard PCI-DSS 3.2 , ISO 25010, ISO 27001, etc.
Executive and Detailed reports available in English, Spanish, Russian and Italian. We will translate those reports to your own language
COPYRIGHT (C) 2014-2021 SECURITY REVIEWER SRL. ALL RIGHTS RESERVED.