With Dynamic Reviewer Safe-PenTest module, you can inspect your Web Application during running, directly using your Browser, in non-invasive way.
DAST-Penetration Testing made easy
The following installation options are available:
Web App. You can install it at your premises, installable in any host OS supporting Docker.
Team Reviewer Plugin. BlackBox DAST plugin. Team Reviewer pre-installed is required.
Cloud App. Like a local installed app, it provides various Usage Modes and Connection Modes.
Its special Safe-PenTest feature, allowing to explore vulnerabilities in your Web Applications, at the same time to keeping them securely. No need of Backups before PenTest, we guarantee our tool will keep your system and database integrity.
You can import third-party results from Security Scanners, Host Scanners and Proof-of-Exploits tools. Their results will be correlated automatically and a unified Enterprise Report is generated.
Dynamic Reviewer DAST provides a robust and stable framework for Web Application Security Testing, suitable for all Security Analysts, QA and Developers with False Positives and False Negatives support, offering an easy-to-use Web GUI, Advanced Scan and Enterprise Reporting capabilities.
Usage Modes
Dynamic Reviewer Provides two usage modes:
Black Box mode. It is placed in the role of the average hacker, with no internal knowledge of the target system. Testers using Dynamic Reviewer are not provided with any architecture diagrams or source code that is not publicly available. Dynamic Reviewer determines the vulnerabilities in a system that are exploitable from outside the network.
This means that Black-Box penetration testing relies on dynamic analysis of currently running programs and systems within the target network.
Dynamic Reviewer follows the OWASP Web Security Testing Guide, chapter 4. Web Application Security Testing.
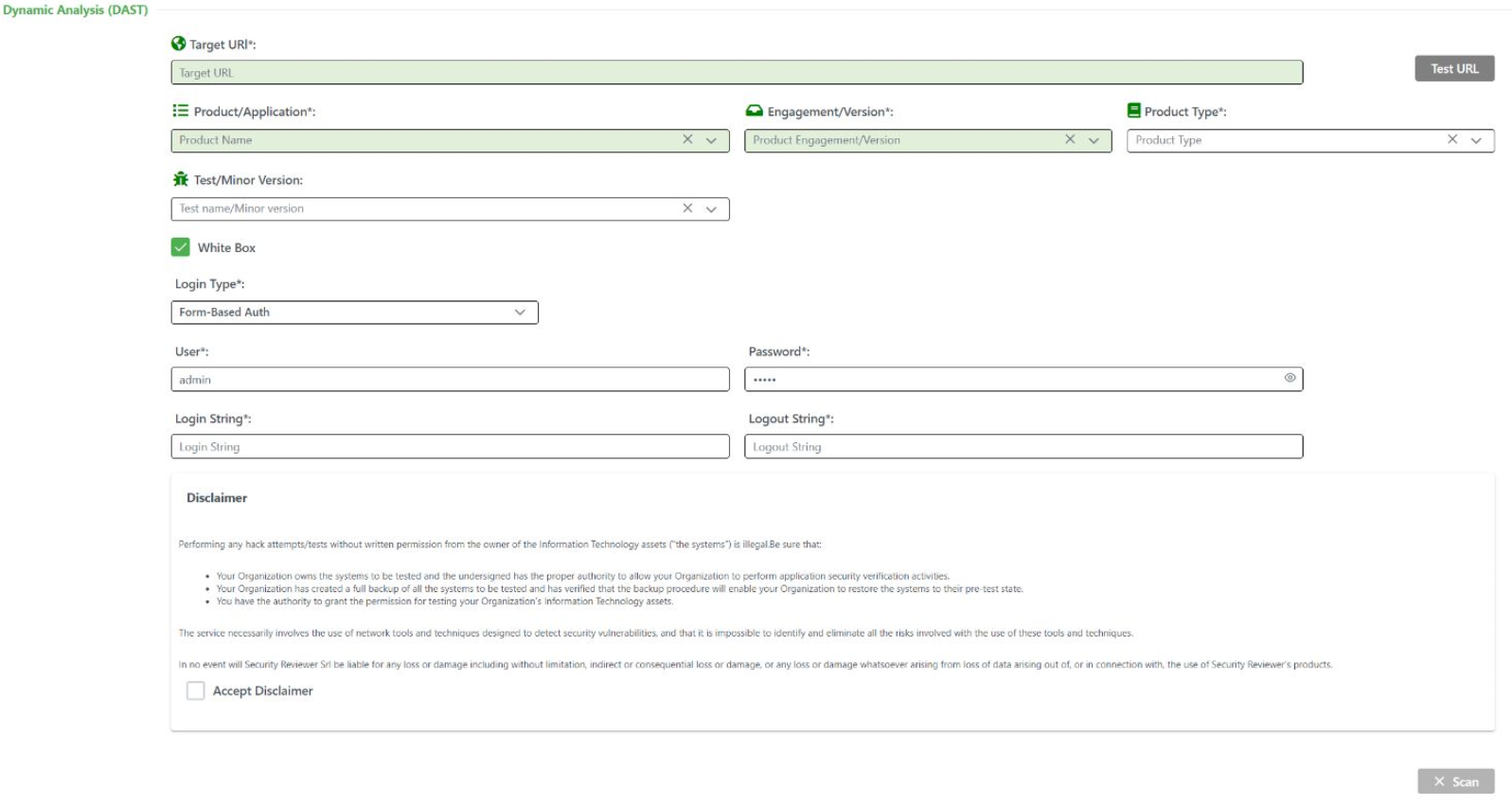
Further, Dynamic Reviewer analyzes in deep the client-side code (Ajax, DOM, JavaScript, TypeScript, etc.) discovering the largest number of client-side vulnerabilities in the market.White Box mode. [Cloud only] It performs Authentication before starting the scan. It provides the following Login modes:
Form-Based Authentication: login with User and Password as Web form, You can configure more than one user, they will be tested all.
JSON-Based Authentication: submit a JSON object with credentials
Tokern-Based Authentication: You can modify the request headers for inserting tokens
Script-Based Authentication: upload and execute a custom script used to login
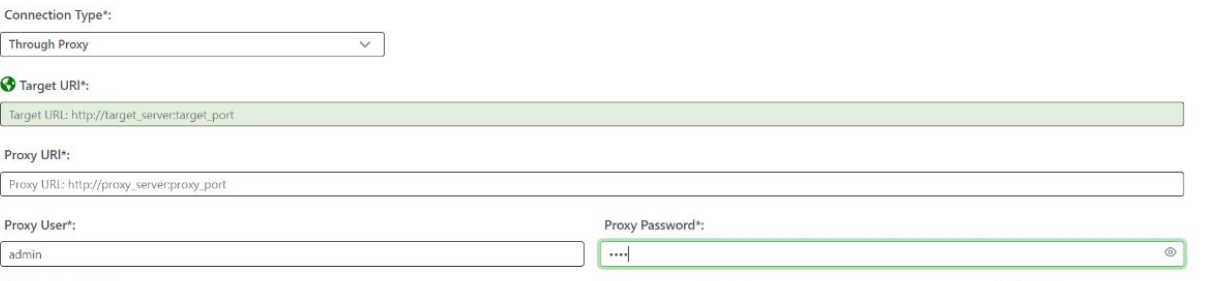
Connection Modes
Both on premises and Cloud installations can connect to the target Web Application in different modes:
Direct. Dynamic Reviewer will reach the target Web Application using a Direct connection to Internet
Through Proxy. For reaching the target Web Application you need a proxy. You can configure the Proxy URI, Proxy TCP Port, Proxy User and Proxy Password
SSH Tunnelling. A temporary SSH key will be automatically generated for the current Scan. The User can download it and execute the commands shown in the screen. It will create a SSH Tunnel to reach the target Web Application.
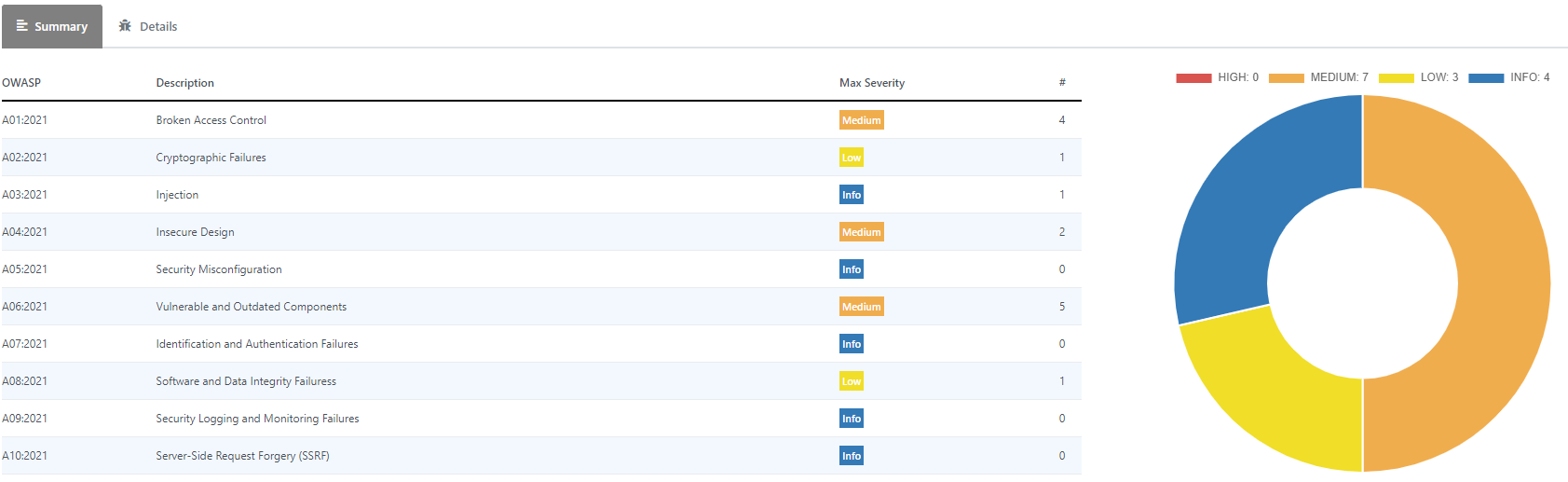
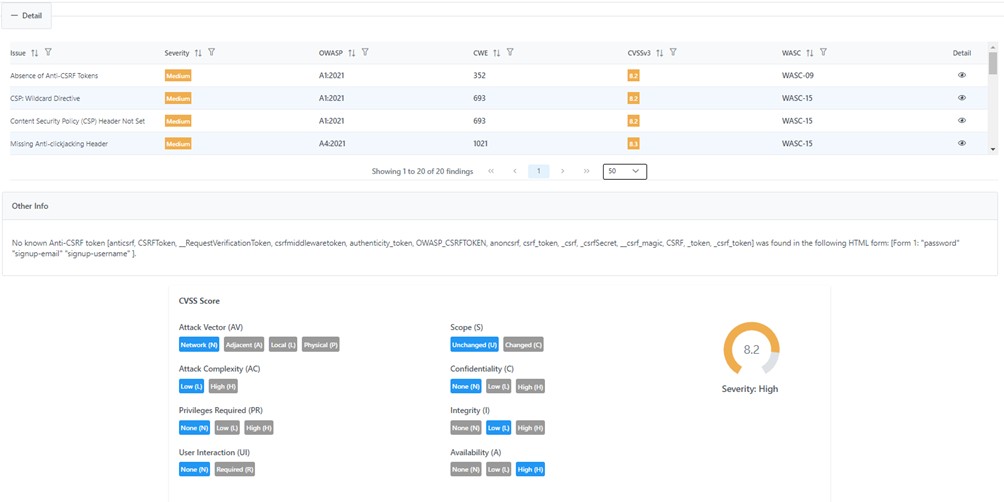
Findings
Once Scan is terminated, you have a list of Findings. You can:
Suppress a Finding Category (example: all Blind SQL Injection issues)
Suppress one or more Findings inside a Category
Add Comments to the entire scan, to a Finding Category, to a single Finding
Modify, Delete, change Severity tag, Merge Findings
Import Results from third-party tools
Export Combined Results in PDF, HTML, JSON, CSV, Excel and Word format
Add Evidences to the Findings
You can drill-down to every Threats' category:
Each Category groups more vulnerablities found in the virtual Attacks:
We call such Attack ‘virtual’ because Dynamic Reviewer does not really execute the attack/exploit, but simulate it only.
Further, instead of declaring hundreds or even thousands of vulnerabilities you can focus of their categories.
Powered By
Dynamic Reviewer is Powered By the following open source tools:
OWASP ZAP (Proxy)
p0f, DataSploit (Fingerprinting)
pWeb, Enlightn, Magescan, Droopescan, Joomscan, Typo3scan(Wordpress, Laravel, Magento, Drupal, Joomla, TYPO3, and other PHP CMS Discovery)
wXf, SearchSploit (Ready-to-use Web Exploits)
DirSearch (SiteMap)
OSVDB, NVD, GHSA, RUSTSEC, PYUP, ALPINE (Vulnerability Databases)
retireJS (Outdated and vulnerable JavaScript and TypeScript 3rd-party libraries detection)
0d1n (Login brute-force)
John The Ripper (Password recovery and cracking)
Wfuzz, WebFormFuzzer, SQLInjectionFuzzer, FuzzAPI (Web Application and REST API Fuzzers)
SQLMap (SQL Injection and DB takeover)
Selenium (WebDrivers for Crawling)
All vulnerabilities resulting from the above OSS tools, will be collected and correlated and included in the Dynamic Reviewer results.
Security Scanners
Further the above listed tools, Dynamic Reviewer provides its own Security Scan Engine, but you can also add results coming from third-party Security Scanners in order to cover possible False Negatives.
We currently support a number of 3rd-party Security Scanners.
Each Security Scanner makes different fields available.
In order to be able to combine output from multiple tools, our Plugin Manager lets you map between the fields provided by each Security Scanner and those you care about for your report.
It is up to you to purchase and manage the required Security Scanner’s License in case of you are using a Commercial Product.
Our tool imports the results only, without running your Security Scanner.
Team Collaboration
Being powered by Team Reviewer, with Dynamic Reviewer you can:
Share a common view of the entire project so that the team can work together towards a common goal
Each person can work on a different project or as part of a team. Changes made by any member of the team are automatically pushed to all the others
Compare different versions of the Issues in your project. Use the line-by-line breakdown to quickly see what was changed
Our Own Security Scan Engine
Main features:
Technology Discovery
Port scanning, Services Discovery (no need of nmap or nessus)
Audit, Bruteforce, Evasion, grep ancd Mangle modes
Cookie-jar/cookie-string support.
Custom header support.
SSL support with fine-grained options.
User Agent spoofing.
HTTP/2 support.
Proxy support for SOCKS4, SOCKS4A, SOCKS5, HTTP/1.1 and HTTP/1.0.
Proxy authentication.
Site authentication (SSL-based, form-based, Cookie-Jar, Basic-Digest, NTLMv1, Kerberos and others).
Automatic log-out detection and re-login during the scan (when the initial login was performed via the
autologin,login_scriptorproxyplugins).Custom 404 page detection.
UI abstraction:
Command-line Interface.
Web User Interface.
Pause/resume functionality.
Hibernation support -- Suspend to and restore from disk.
High performance asynchronous HTTP requests.
With adjustable concurrency.
With the ability to auto-detect server health and adjust its concurrency automatically.
Support for custom default input values, using pairs of patterns (to be matched against input names) and values to be used to fill in matching inputs.
Discovery Mode
Through Passive Fingerprinting it provides discovery of: Host OS, Web Server, Application Server, DB type, CMS, Directory bruteforce, DNS WildCard, domain_dot, .NET Errors, Favicon identification, Backdoors, Captchas, DVCS, GIt/Svn files, Fingerprint BING, Fingerprint Google, Fingerprint PKS, Fingerprint WAF, GHDB, Google Spider, Halberd, HMAP, HTTPS over HTTP, Import Results, Oracle discovery, Phish Tank, phpeggs, phpinfo, pykto, RIA Enumerator, robots.txt reader, Server Header, Server Status, Shared Hosting, SiteMap Reader, Splash, spiderMan, URL Fuzzer, urllist.txt Reader, userDir, webDiff, webSpider, wordNet, Wordpress Fingerprint, Laravel Vulnerabilities, WDSL Finder, XSSedDotCom, Yahoo Site Explorer, zone_h.
Audit mode
Audit of LDAP, Blind SQL Injection. Buffer Overflow, webDAV, eval, file Upload, format String vulnerability, legacy FrontPage web apps, Global Redirect, HTA Access Methods, Local File Include, mx Injection, OS Command Injection, Phishing attack vector, preg_replace, re-DoS, Remote File Include, Respnse Splitting, SQL Injection, Server-Side Injection, Weak SSL Certificate, Unsecure Connection, Xpath Injection, XSRF, Cross-Site Scripting (XSS), XST.
Bruteforce Mode
Usage of Bruteforce for: Basic Authentication and Web Form Authentication.
Evasion Mode
Seeking for: backSpace Between Dots, full Width Encode, modsecurity, reversed Slashes, rndCase, rndHexEncode, rndParam, rndPath, sel Reference, shift out-shift in Between Dots.
Grep Mode
Find: Ajax, blank Body, Code Disclosure, Collect Cookies, Credit Cards, Directory Indexing, DOM XSS, .NET Event Validation, Error 500, Error Pages, Feeds, File Upload, Comments, Form Autocomplete, e-mails. Hashes, HTTP Auth detect, HTTP in Body, language, Meta Tags, motw, Objects, Oracle, Password Profiling, Path Disclosure, Private IPs, SSN, Strage HTTP Code, Strange Headers, Strange Reason, SVN Users, User-defined Regex, WDSL Grepper.
Mangle Mode
Usage of Stream Editor (sed) for pattern matching: Privilege Escalation, Exploiting sudo/administrator rights, DirtyPipe (CVE 2022-0847), Windows Privilege Escalation: PrintNightmare.
Client-Side scanning
Dynamic Reviewer includes an integrated, real browser environment in order to provide sufficient coverage to modern web applications which make use of technologies such as HTML5, JavaScript, DOM manipulation, AJAX, etc.
In essence, this turns Dynamic Reviewer into a DOM and JavaScript debugger, allowing it to monitor DOM events and JavaScript data and execution flows. As a result, not only can the system trigger and identify DOM-based issues, but it will accompany them with a great deal of information regarding the state of the page at the time.
Relevant information include:
Page DOM, as HTML code.
With a list of DOM transitions required to restore the state of the page to the one at the time it was logged.
Original DOM (i.e. prior to the action that caused the page to be logged), as HTML code.
With a list of DOM transitions.
Data-flow sinks -- Each sink is a JS method which received a tainted argument.
Parent object of the method (ex.:
DOMWindow).Method signature (ex.:
decodeURIComponent()).Arguments list.
With the identified taint located recursively in the included objects.
Method source code.
JS stacktrace.
Execution flow sinks -- Each sink is a successfully executed JS payload, as injected by the security checks.
Includes a JS stacktrace.
JavaScript stack-traces include:
Method names.
Method locations.
Method source codes.
Argument lists.
Compatible with ES5 and ES6
Integrated with Wapplyzer
A bunch of frameworks are supported, like Cordova/Phonegap and Node.js
In essence, you have access to roughly the same information that your favorite debugger (for example, FireBug) would provide, as if you had set a breakpoint to take place at the right time for identifying an issue.
DOM Security Issues
The list of DOM Security Issues found by Dynamic Reviewer are:
# | Issue | Type | Category |
1 | Code Injection - Client Side | Error | Code Execution |
2 | Code Injection - PHP input wrapper | Error | Code Execution |
3 | Code injection - Timing | Error | Code Execution |
4 | File Inclusion - Client Side | Error | Code Execution |
5 | OS Command Injection - Client Side | Error | Code Execution |
6 | OS Command Injection - Timing | Error | Code Execution |
7 | Remote File Inclusion Client Side | Error | Code Execution |
8 | Session Fixation | Error | Code Execution |
9 | XSS - DOM | Error | Code Execution |
10 | XSS - DOM - Script Context | Error | Code Execution |
11 | XSS - Event | Error | Code Execution |
12 | Data from attacker controllable navigation based DOM properties is executed as HTML | Error | Code Execution |
13 | Data from attacker controllable navigation based DOM properties is executed as JavaScript | Error | Code Execution |
14 | Data from attacker controllable URL based DOM properties is executed as HTML | Error | Code Execution |
15 | Data from attacker controllable URL based DOM properties is executed as JavaScript | Error | Code Execution |
16 | Non-HTML format Data from DOM storage is executed as HTML | Warning | Code Execution |
17 | Non-JavaScript format Data from DOM storage is executed as JavaScript | Warning | Code Execution |
18 | HTML format Data from DOM storage is executed as HTML | Info | Code Execution |
19 | JavaScript format Data from DOM storage is executed as JavaScript | Info | Code Execution |
20 | Data from user input is executed as HTML | Warning | Code Execution |
21 | Data from user input is executed as JavaScript | Warning | Code Execution |
22 | Non-HTML format Data taken from external site(s) (via Ajax, WebSocket or Cross-Window Messages) is executed as HTML | Error | Code Execution |
23 | Non-JavaScript format Data taken from external site(s) (via Ajax, WebSocket or Cross-Window Messages) is executed as JavaScript | Error | Code Execution |
24 | HTML format Data taken from external site(s) (via Ajax, WebSocket or Cross-Window Messages) is executed as HTML | Warning | Code Execution |
25 | JavaScript format Data taken from external site(s) (via Ajax, WebSocket or Cross-Window Messages) is executed as JavaScript | Warning | Code Execution |
26 | Non-HTML format Data taken from across sub-domain (via Ajax, WebSocket or Cross-Window Messages) is executed as HTML | Warning | Code Execution |
27 | Non-JavaScript format Data taken from across sub-domain (via Ajax, WebSocket or Cross-Window Messages) is executed as JavaScript | Warning | Code Execution |
28 | HTML format Data taken from across sub-domain (via Ajax, WebSocket or Cross-Window Messages) is executed as HTML | Info | Code Execution |
29 | JavaScript format Data taken from across sub-domain (via Ajax, WebSocket or Cross-Window Messages) is executed as JavaScript | Info | Code Execution |
30 | Non-HTML format Data taken from same domain (via Ajax, WebSocket or Cross-Window Messages) is executed as HTML | Warning | Code Execution |
31 | Non-JavaScript format Data taken from same domain (via Ajax, WebSocket or Cross-Window Messages) is executed as JavaScript | Warning | Code Execution |
32 | HTML format Data taken from same domain (via Ajax, WebSocket or Cross-Window Messages) is executed as HTML | Info | Code Execution |
33 | JavaScript format Data taken from same domain (via Ajax, WebSocket or Cross-Window Messages) is executed as JavaScript | Info | Code Execution |
34 | Weak Hashing algorithms are used | Error | Cryptography |
35 | Weak Encryption algorithms are used | Error | Cryptography |
36 | Weak Decryption algorithms are used | Error | Cryptography |
37 | Cryptographic Hashing Operations were made | Info | Cryptography |
38 | Encryption operations were made | Info | Cryptography |
39 | Decryption operations were made | Info | Cryptography |
40 | Potentially Sensitive Data is leaked (via HTTP, Ajax, WebSocket or Cross-Window Messages) | Error | Data Leakage |
41 | Potentially Sensitive Data is leaked through Referrer Headers | Error | Data Leakage |
42 | Data is leaked through HTTP | Warning | Data Leakage |
43 | Data is leaked through WebSocket | Warning | Data Leakage |
44 | Data is leaked through Cross-Window Messages | Warning | Data Leakage |
45 | Data is leaked through Referrer Headers | Warning | Data Leakage |
46 | Potentially Sensitive Data is stored on Client-side Storage (in LocalStorage, SessionStorage, Cookies or IndexedDB) | Warning | Data Storage |
47 | Data is stored on Client-side Storage (in LocalStorage, SessionStorage, Cookies or IndexedDB) | Info | Data Storage |
48 | Cross-window Messages are sent insecurely | Error | Communication |
49 | Cross-site communications are made | Warning | Communication |
50 | Communications across sub-domains are made | Warning | Communication |
51 | Same Origin communications are made | Info | Communication |
52 | JavaScript code is loaded from Cross-site Sources | Warning | JS Code |
53 | JavaScript code is loaded from across sub-domains | Info | JS Code |
54 | JavaScript code is loaded from Same Origin | Info | JS Code |
Configuration options include:
Adjustable pool-size, i.e. the amount of browser workers to utilize.
Timeout for each job.
Worker TTL counted in jobs -- Workers which exceed the TTL have their browser process re-spawned.
Ability to disable loading images.
Adjustable screen width and height.
Can be used to analyze responsive and mobile applications.
Ability to wait until certain elements appear in the page.
Configurable local storage data.
Coverage
The system can provide great coverage to modern web applications due to its integrated browser environment. This allows it to interact with complex applications that make heavy use of client-side code (like JavaScript) just like a human would.
In addition to that, it also knows about which browser state changes the application has been programmed to handle and is able to trigger them programmatically in order to provide coverage for a full set of possible scenarios.
By inspecting all possible pages and their states (when using client-side code) Dynamic Reviewer is able to extract and audit the following elements and their inputs:
Forms
Along with ones that require interaction via a real browser due to DOM events.
User-interface Forms
Input and button groups which don't belong to an HTML
<form>element but are instead associated via JS code.
User-interface Inputs
Orphan
<input>elements with associated DOM events.
Links
Along with ones that have client-side parameters in their fragment, i.e.:http://example.com/#/?param=val¶m2=val2
With support for rewrite rules.
Link Templates -- Allowing for extraction of arbitrary inputs from generic paths, based on user-supplied templates -- useful when rewrite rules are not available.
Along with ones that have client-side parameters in their URL fragments, i.e.:http://example.com/#/param/val/param2/val2
Cookies
Headers
Generic client-side elements which have associated DOM events.
AJAX-request parameters.
JSON request data.
XML request data.
Web Security Issues
Dynamic Reviewer runs testing to identify all of the major web application security vulnerabilities, such as SQL Injection, Cross-Site Scripting, Cross Site Request Forgery, and more. Dynamic Reviewer has an ever growing list of tests that are run against the application and APIs to identify potential security vulnerabilities.
Dynamic Reviewer provides the following HTTP passive and active scan rules which find specific vulnerabilities. Dynamic Reviewer can discover the following OWASP ZAP Web Security Issues:
Id | Ossue | Risk | Type |
|---|---|---|---|
Medium | Active | ||
Low | Passive | ||
Medium | Passive | ||
High | Active | ||
High | Active | ||
High | Active | ||
Medium | Active | ||
High | Active | ||
High | Passive | ||
High | Passive | ||
Low | Passive | ||
Low | Passive | ||
Informational | Passive | ||
High | Passive | ||
Low | Passive | ||
Informational | Passive | ||
High | Passive | ||
Medium | Passive | ||
Medium | Passive | ||
Medium | Passive | ||
Medium | Passive | ||
Low | Passive | ||
Low | Passive | ||
Informational | Passive | ||
Information Disclosure - Sensitive Information in HTTP Referrer Header | Informational | Passive | |
High | Passive | ||
Informational | Passive | ||
Medium | Passive | ||
Medium | Passive | ||
Medium | Passive | ||
Medium | Passive | ||
Medium | Passive | ||
Medium | Passive | ||
Medium | Passive | ||
Low | Passive | ||
High | Passive | ||
High | Passive | ||
Informational | Passive | ||
High | Passive | ||
High | Passive | ||
High | Passive | ||
High | Passive | ||
Server Leaks Information via 'X-Powered-By' HTTP Response Header Field(s) | Low | Passive | |
High | Passive | ||
High | Passive | ||
High | Passive | ||
High | Passive | ||
High | Passive | ||
High | Passive | ||
Big Redirect Detected (Potential Sensitive Information Leak) | High | Passive | |
High | Active | ||
Medium | Passive | ||
Low | Active | ||
High | Active | ||
Medium | Passive | ||
Medium | Passive | ||
Medium | Active | ||
Medium | Passive | ||
Medium | Active | ||
Low | Passive | ||
Medium | Passive | ||
Low | Passive | ||
Informational | Passive | ||
Informational | Active | ||
Low | Passive | ||
Medium | Passive | ||
Medium | Passive | ||
Medium | Passive | ||
Medium | Passive | ||
Medium | Active | ||
Low | Passive | ||
Medium | Passive | ||
Medium | Passive | ||
High | Passive | ||
Informational | Passive | ||
Informational | Active | ||
High | Passive | ||
Medium | Active | ||
High | Active | ||
Medium | Passive | ||
Medium | Passive | ||
Medium | Passive | ||
Medium | Passive | ||
Medium | Active | ||
Informational | Active | ||
High | Active | ||
High | Active | ||
High | Active | ||
High | Active | ||
High | Active | ||
Medium | Active | ||
Medium | Active | ||
Medium | Active | ||
Medium | Active | ||
Medium | Active | ||
High | Active | ||
High | Active | ||
High | Active | ||
High | Active | ||
High | Active | ||
Informational | Active | ||
Informational | Active | ||
High | Active | ||
High | Active | ||
High | Active | ||
High | Active | ||
High | Active | ||
Informational | Active | ||
High | Active | ||
Medium | Active | ||
High | Active | ||
High | Active | ||
Medium | Active | ||
Medium | Active | ||
High | Active | ||
Medium | Active | ||
High | Active | ||
Medium | Active | ||
Medium | Active | ||
Medium | Active | ||
Medium | Active | ||
Medium | Active | ||
Informational | Active | ||
Informational | Active | ||
Medium | Active | ||
High | Active | ||
Medium | Active | ||
Medium | Active | ||
High | Active | ||
High | Active | ||
High | Active | ||
Medium | Active | ||
High | Active | ||
Medium | Passive | ||
Medium | Passive | ||
High | Passive | ||
High | Passive | ||
Low | Passive | ||
Low | Passive | ||
Low | Passive | ||
Informational | Passive | ||
Medium | Active | ||
High | Active | ||
High | Active | ||
High | Active | ||
High | Active | ||
Medium | Passive | ||
High | Active | ||
High | Active | ||
High | Active | ||
High | Active | ||
Informational | Active | ||
Medium | Active | ||
High | Active | ||
Informational | Passive | ||
Informational | Passive | ||
High | Active | ||
High | Active | ||
High | Active | ||
Medium | WebSocket Passive | ||
Informational | WebSocket Passive | ||
Low | WebSocket Passive | ||
Informational | WebSocket Passive | ||
High | WebSocket Passive | ||
Low | WebSocket Passive | ||
Informational | WebSocket Passive | ||
Information Disclosure - Suspicious Comments in XML via WebSocket | Informational | WebSocket Passive |
Note that these are examples of the alerts raised - many rules include different details depending on the exact problem encountered. For example, it covers also: Text4Shell (CVE-2022-42889), Insufficient Site Isolation Against Spectre Vulnerability
Passive scans
Thay review all HTTP requests and responses from the application, looking for indicators of security vulnerabilities. These scans do not change anything about the requests.
Passive Fingerprinting
Whenever Dynamic Reviewer obtains a fingerprint from the observed traffic, passing through any firewall, it identifies the Operating System and obtain some ancillary data needed for other analysis tasks.
For TCP/IP, the tool fingerprints the client-originating SYN packet and the first SYN+ACK response from the server, paying attention to factors such as the ordering of TCP options, the relation between maximum segment size and window size, the progression of TCP timestamps, and the state of about a dozen possible implementation quirks (e.g. non-zero values in "must be zero" fields). The metrics used for application-level traffic vary from one module to another; where possible, the tool relies on signals such as the ordering or syntax of HTTP headers or SMTP commands, rather than any declarative statements such as User-Agent. Application-level fingerprinting modules currently support HTTP, SMTP, FTP, POP3, IMAP, SSH, and SSL/TLS. Some of its capabilities include:
- Highly scalable and extremely fast identification of the operating system and software on both endpoints of a vanilla TCP connection - especially in settings where NMap probes are blocked, too slow, unreliable, or would simply set off alarms,
- Measurement of system uptime and network hookup, distance (including topology behind NAT or packet filters), and so on.
- Automated detection of connection sharing / NAT, load balancing, and application-level proxying setups.
- Detection of dishonest clients / servers that forge declarative statements such as X-Mailer or User-Agent.
Active scans
On the other hand, they will create and modify requests being sent to the application, sending test requests that will surface vulnerabilities that would not be caught in a passive scan.
Active scans are definitely a better way to test for vulnerabilities in your application, as the test suite injects requests that will surface vulnerabilities. These scans are, however, actively attempting to attack the application, which may include creating or deleting data.
Fuzzing
Fuzzing is a technique of submitting lots of invalid or unexpected data to a target.
Dynamic Reviewer allows you to fuzz any request still using:
A built-in set of Payloads. Payload Generators generate the raw attacks that the fuzzer submits to the target application
Payload Processors are used to automatically change specific payloads before they are submitted
Fuzz Location Processors are used to automatically change all of the payloads before they are submitted
Custom scripts can be uploaded
HOST SCANNING
Dynamic Reviewer is integrated with the following third-party Host Scanning tools:
Tenable Nessus (Commercial)
Rapid7 Nexpose (Commercial)
The Dynamic Reviewer and thrid-party tool results will be automatically correlated for obtaining a unique results and a unified report.
PROOF-OF-EXPLOITS
Dynamic Reviewer is a DAST tool, it can detect all vulnerabilities of your site and list all possible Exploits. It won’t execute those Exploits.
If you need a full Penetration Test that includes the Exploits, you need more than one tool.
The Penetration Testing process requires an extensive set of tools. These include network (Host Scanning) and vulnerability scanning software, as well as tools that can launch specific attacks and exploits such as brute-force attacks or SQL injections, a custom reporting and a unified dashboard.
The final and most important stage of a Penetration Test is the Enterprise Report. This is a detailed report to be shared with the target company’s security team. It documents the pentesting process, vulnerabilities discovered (including the ones at client-side), proof that they are exploitable, and actionable recommendations for remediating them.
Internal teams can then use this information to improve security measures and remediate vulnerabilities. This can include patching vulnerable systems. These upgrades include rate limiting, new firewall or WAF rules, DDoS mitigation, and stricter form validation.
Dynamic Reviewer is fully integrated with Invicti Acunetix and PenTera ASV for generating proof-of-exploits and a unified Enterprise Report, multi-lingual and fully customizable for the customer’s needs, and provides a unified dashboard, based on OWASP defectDojo.
REST API
Very simple and straightforward API.
Easy interoperability with non-Ruby systems.
Operates over HTTP.
Uses JSON to format messages.
ENTERPRISE REPORTING
Dynamic Reviewer provides:
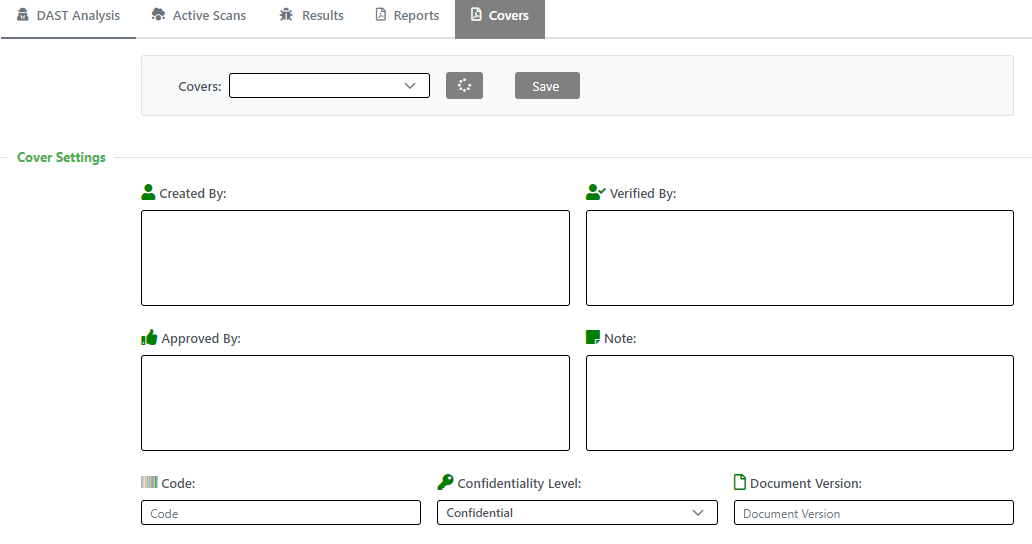
Detailed Report. A standard DAST automatically-generated technical report in PDF, Word, Excel and HTML formats, listing all detailed information necessary for Indentifying and Remediate the vulnerabilities. Fully customizable ISO 9001-compliant Cover Pages, can be saved as different Profiles
You can upload two logos, and define the ISO 9001 responsability chain (Created By, Verified By, Approved By. You can add a Disclaimer Note, a ISO template code, the Confidentiality Level and a Document version.
Enterprise Report. Fully-customized automatically-generated Executive Summary and Technical reports, starting from a customer-driven Form Template (on which customized tags will be filled), Word template, written in the preferred language (Report template in Word format, containg the custom tags).
Best Performances
Scan-times using traditional tools can range between a few hours to a couple of weeks – maybe even more. This means that wasted time can easily pile up, even when we’re talking about mere milliseconds per request/response.
Dynamic Reviewer benefits from great network performance due to its asynchronous HTTP request/response model. In this case – and from a high-level perspective –, asynchronous I/O means that you can schedule operations in such a way that they appear like they’re happening at the same time, which in turn means higher efficiency and better bandwidth utilization. That means:
Faster hyperlink processing
Faster numbering processing
Faster screenshot processing
It provides a high-performance environment for the tests that need to be executed while making adding new tests very easy. Thus, you can rest assured that the scan will be as fast as possible and performance will only be limited by your or the audited server’s physical resources.
Avoiding useless technical details, the gist is the following:
Every type of resource usage has been massively reduced — CPU, RAM, bandwidth.
CPU intensive code has been rewritten and key parts of the system are now 2 to 55 times faster, depending on where you look.
The scheduling of all scan operations has been completely redesigned.
DOM operations have been massively optimized and require much less time and overall resources.
Suspension to disk is now near instant.
Previously browser jobs could not be dumped to disk and had to be completed, which could cause large delays depending on the amount of queued jobs.
Default configuration is much less aggressive, further reducing the amount of resource usage and web application stress.
Talk is cheap though, so let’s look as some numbers under Linux:
Duration | RAM | HTTP requests | HTTP requests/second | Browser jobs | Seconds per browser job | |
|---|---|---|---|---|---|---|
Dynamic Reviewer | 00:02:14 | 150MB | 14,504 | 113.756 | 211 | 1.784 |
Best Competitor | 00:06:33 | 210MB | 34,109 | 101.851 | 524 | 3.88 |
Large real production site (cannot disclose) | ||||||
|---|---|---|---|---|---|---|
Duration | RAM | HTTP requests | HTTP requests/second | Browser jobs | Seconds per browser job | |
Dynamic Reviewer | 00:45:31 | 617MB | 60,024 | 47.415 | 9404 | 2.354 |
Best Competitor | 12:27:12 | 1,621MB | 123,399 | 59.516 | 9180 | 48.337 |
As you can see, the impact of the Performances' improvements becomes more substantial as the target’s complexity and size increases, especially when it comes to scan duration and RAM usage — and for the production site the new engine consistently yielded better coverage, which is why it performed more browser jobs.
End result:
Runs fast on under-powered machines.
You can run many more scans at the same time.
You can complete scans many times faster than before.
If you’re running scans in the “cloud”, it means that it’ll cost you many, many times less than before.
Machine Learning
The ML is what enables Dynamic Reviewer to learn from the scan it performs and incorporate that knowledge, on the fly, for the duration of the audit.
It uses various techniques to compensate for the widely heterogeneous environment of web applications. This includes a combination of widely deployed techniques (taint-analysis, fuzzing, differential analysis, timing/delay attacks) along with novel technologies (rDiff analysis, modular meta-analysis) developed specifically for the framework.
This allows the system to make highly informed decisions using a variety of different inputs; a process which diminishes false positives and even uses them to provide human-like insights into the inner workings of web applications.
Dynamic Reviewer is aware of which requests are more likely to uncover new elements or attack vectors and adapts itself accordingly.
Also, components have the ability to individually force the Core Engine to learn from the HTTP responses they are going to induce thus improving the chance of uncovering a hidden vector that would appear as a result of their probing.
DISCLAIMER: Due we make use of open source components (OWASP ZAP, w3af, pWeb, p0f, wXf, OSVDB), we do not sell the product, but we offer a yearly subscription-based Commercial Support, plus our Commercial Security Scanner.