Static Reviewer, Software Composition Analysis, Firmware Reviewer and Team Reviewer provide a Command Line Interface (CLI) for easy integrating on supported and unsupported CI/CD Platform.
Static Reviewer
Using the Static Reviewer Command Line Interface, you can:
Include Security Reviewer in your Secure Development Life Cycle (SDLC)
Perform a pre-build automated Static Analysis
Execute a Multiple Static Analysis (Multi-Analysis) of different types on different applications
While you execute an Analysis of an application with Command Line Interface, you can do other tasks with Security Reviewer graphic interface or Jenkins plugin simultaneously.
CLI command are written in .NET Core, available for Windows and Linux. They can be included in .bat and .sh as well as in CI/CD Pipeline.
Using the Command Line Interface, you can:
Include Static Reviewer in your DevOps
Set Team Reviewer’s connection
Set Language Options via CLI
Execute a Multiple Static Analysis (Multi-Analysis) of different types on different applications, written in different languages
Command Line Interface is provided through some basic commands:
SRCheck
To launch the Scan. It provides the following arguments:
Mandatory Arguments
-a APPLICATION -v VERSION -p FOLDERTOSCAN -r RULESET
Where:
APPLICATION is the name of the App you want to scan. If contains spaces or “-“ must be double quoted
VERSION. Version of App. If contains spaces or “-“ must be double quoted
FOLDERTOSCAN pathname of the source code folder to scan. If contains spaces or “-“ must be double quoted
RULESET can be CWE, OWASP, OWASP2021
Additional Arguments
-c COMPONENTS -s FPS -d FPD -e EXCLUSIONS -w ALM -m -x -n -o -f CUSTOMSEC -q CUSTOMDEAD
Where:
-m, --mobile in case of Mobile App
-x, --noexclusion do Not Apply Exclusions
-n, --skippdf to skip PDF reports creation
-o, --onlysec Security Analysis only
-f, --customsec Custom Security Ruleset
-q, --customdead Custom Dead Code-Best Practices Ruleset
COMPONENTS pathname of Components XML file. If the path contains spaces or “-“must be double quoted. See related section above.
FPS pathname of Security False Positives CSV file, to be imported from a previous scan. If the path contains spaces or “-“ must be double quoted
FPD pathname of Dead Code-Best Practices False Positives CSV file, to be imported from a previous scan. If the path contains spaces or “-“ must be double quoted
EXCLUSIONS pathname of Exclusion txt file, to be imported from a previous scan. If the path contains spaces or “-“ must be double quoted. See related section above.
ALM pathname of Components XML file. If the path contains spaces or “-“ must be double quoted. See related section above.
CUSTOMSEC Path of custom ruleset (.rls) for Security Analysis
CUSTOMDEAD Path of custom ruleset (.rls) for Dead Code-Best Practices Analysis
Informational Arguments
--help Display the Usage screen
--version Display version information
-l, --silent Silent Mode
-g, --debug Debug Mode
Team Reviewer Arguments
In case you purchased Team Reviewer, some additional arguments are available to SRCheck:
-t, --tenant Tenant name (Default: USER, in case of mono-tenant)
-u, --update Update Results on Team Reviewer
-b, --pType Product Type (Only with -u and if omitted = User Group)
-T, --truri Override Team Reviewer URL usually set with SRsetCNF command (see below)
-P, --port Override Team Reviewer Port usually set with SRsetCNF command (see below)
-K, --apikey Override API Key usually set with SRsetCNF command (see below)
-U, --proxyuser Override Proxy User
-W, --proxypasswd Override Proxy Password
-I, --proxyuri Override Proxy URL
-X, --proxyport Override Proxy Port
SRsetCNF
Sets the Team Reviewer Connection Configuration. Please note that each argument needs “=”.
Mandatory Arguments
SRsetCNF -url=TEAMREVIEWERURL -tcpport=TEAMREVIEWERPORT –api=APIKEY
Where:
-url Team Reviewer URL
-tcpport Team Reviewer TCP Port
–api Your personal API Key to connect to Team Reviewer
Additional Arguments
In case you have a multi-tenant Team Reviewer configuration:
-tenant Team Reviewer tenant name
-add Add a Team Reviewer tenant by name from your client configuration
-delete Remove a Team Reviewer tenant by name from your client configuration
In case you are connected to Team Reviewer through a Proxy, the following optional arguments are available:
-proxy=PROXYIP -proxyport=PROXYTCPPORT -user=USERNAME -pwd=PASSWORD
SRsetOPT
SRsetOPT to set the Language Options before scanning for locating Java JDK, COBOL copybooks folder, and Ruby executable. Please note that each argument needs “=”. It provides the following arguments:
-l=LANGUAGE -p=PATH
Where:
LANGUAGE can be java or cobol or ruby
PATH
For JAVA is the java executable location, for example “C:\Program Files\Java\jdk-11.0.11\bin” or “/usr/bin/”. For Ruby is the Ruby installation path, for example “C:\ruby193” (Not needed under Linux).
For COBOL is the CopyBook folder, for example “D:\_COPY” or ”/home/user1/src/copybooks”.
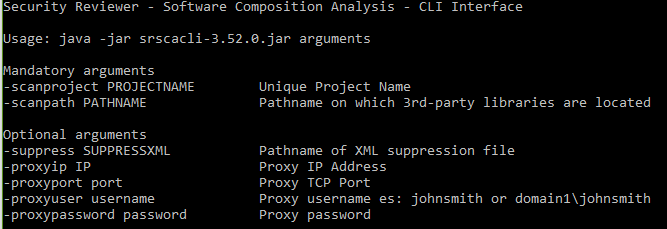
Software Composition Analysis
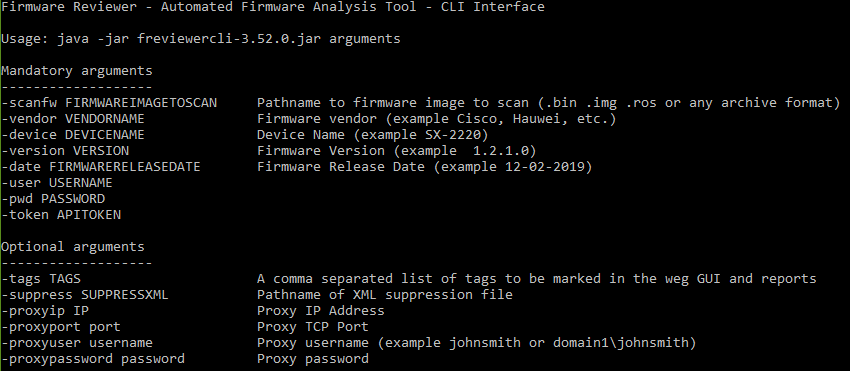
Firmware Reviewer
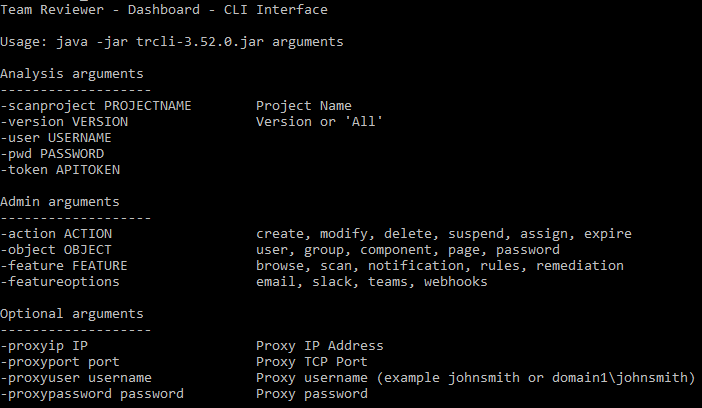
Team Reviewer API Client
Team Reviewer is our default Dashboard. All features provided by the Web GUI are invokable via REST API, including Admin tasks. Team Reviewer provides a JAVA tool for invoking REST API via Command Line.
COPYRIGHT (C) 2014-2022 SECURITY REVIEWER SRL. ALL RIGHTS RESERVED.